The leading data security solution for scattered data – protects data within company boundaries and beyond
ITsMine is a leading solution used by organizations to protect against internal and external threats automatically. ITsMine takes a proactive approach to protecting data within company boundaries and beyond. ITsMine is Agentless and very easy to implement (takes less than a day), does not require additional headcount due to AI and deception techniques used, has a built-in automatic reaction for both Internal and External threats, and can turn any folder into the most secured folder, whether on-premise or in the cloud.
ITsMine tracks, targets, and pinpoints your data regardless of its location. Whether your company’s data is on a personal device, on a remote server, in the cloud, or on an external device or medium, it notifies you in real-time. It allows you to know who has access to your data and where they’re using it at any given moment and the power to control that data—the perfect tool to help you deal with any data breach emergency.

ITsMine Beyond DLP requires no policies and no permanent endpoint agents while guaranteeing protection against internal and external attackers. ITsMine’s Beyond DLP solves the challenges using a fully automated solution with negligible false positives and without affecting employee productivity. ITsMine is a DLP solution to protect against internal and external threats automatically.
We are the distributor for ITsMine in Middle East countries including UAE, Saudi Arabia, Bahrain, Kuwait, Onam & Qatar.
ITsMine is the ONLY platform that has the answer to the most terrifying attack an organization can experience – the new generation of Ransomware (Lockbit 2.0/3.0) that involves data leakage followed by encryption.
With the increasing number of data breaches, current Data Loss Prevention solutions struggle to detect data breaches in real-time, also failing to collect sufficient threat event information after threat detection. At ITsMine, we have focused on solving some of the major issues around putting a DLP solution in place. This includes solving the following headaches faced by organizations looking to effectively protect their data:

Traditional DLP solutions are based on the knowledge that security teams do not – and cannot – have. Moreover, current solutions do not treat the vector of attack – they try to determine if a file supposedly left the company or not, instead of verifying if it is: an external attacker trying to steal company data (or harm it), a rogue employee or an employee that made a mistake. Therefore, current solutions only treat and track the data, failing to provide the needed automatic action for each vector of attack.
Beyond DLP™ automatically plants thousands of SoftwareMines™ around the organization’s file storage, both on-premise and cloud. When a SoftwareMine™ gets opened, the company will immediately receive critical forensic information about the breach. This information can be used to understand exactly what happened in order to improve data security measures within the company and put the control back into the Security Department’s hands.
Due to its automatic detection mode, ITsMine is the only available option that provides real-time breach detection notifications with specific data on the compromised data, location, and time when the breach occurred. This is achieved through the Call Home feature, which ensures that all enterprise documents are protected anywhere in the world. Our innovative approach requires no policies and no permanent endpoint agents, providing the best protection while detecting breaches in real-time.



Beyond DLP™ uses Artificial Intelligence (AI) to understand the severity level and vector of the attack, proactively taking the necessary action to block data loss and obtain critical evidence while guaranteeing protection against internal and external attackers:
From an internal attack perspective, ITsMine detects abnormal behavior and calculates risk levels to automatically block the activity or educate and empower
employees to handle critical data properly.
From the perspective of an external attack, once an attacker evades all the traditional organizational security, and successfully accesses the organizational data network, ITsMine automatically blocks and isolates the compromised endpoint and provides important forensic information to the security department even after data exfiltration.
Continuously track your scattered data’s location, anywhere: on-premise, on personal devices, and in the cloud – with File-GPS™ beacons, transparently embedded into all your sensitive files.
Detect both internal and external data breaches and abnormal use of company data by planting SoftwareMines™ (advanced virtual sensors) in critical areas. Obtain forensic evidence on internal offenders by deploying disposable agents on suspicious endpoints.
Engage employees in your data protection efforts by using integrated Data Security Awareness Training Campaigns and avoiding unnecessary access to data.
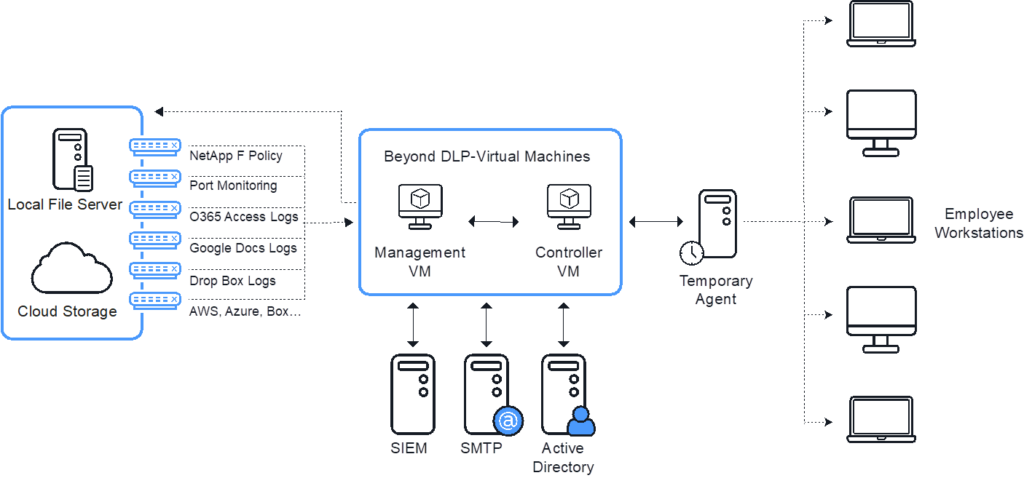
Current solutions on the market are all based on manual policies, which limit the effectiveness and reliability of the solutions. We automatically protect sensitive data in all three states of digital data:

ITsMine monitors and protects data in central file storage (on-premise and cloud) against insider and external attackers including encryption, deletion, change, or data theft. The Transparent evidence Obtainer and Attack Blocker (TOB) protects and monitors data on the endpoint computer HDD, on suspected devices, or when sensitive data exists on the employee’s computer.

the solution is monitoring all downloaded data from file storage, TOB is protecting data that goes out from the endpoint computers, on suspected devices, or when sensitive data exists on the employee’s computer.

Beyond DLP™ monitors any misuse of data from file storage, TOB is protecting data that is created or copied from a sensitive resource, on suspected devices, or when sensitive data exists on the employee’s computer.
All in all, Beyond DLP™ offers organizations the following key benefits:

Protect your business with our expert cybersecurity and cloud services. From penetration testing to compliance and SOC monitoring, we’ve got you covered.
Copyright © 2026 Clouds Dubai, Powered by Oktohut