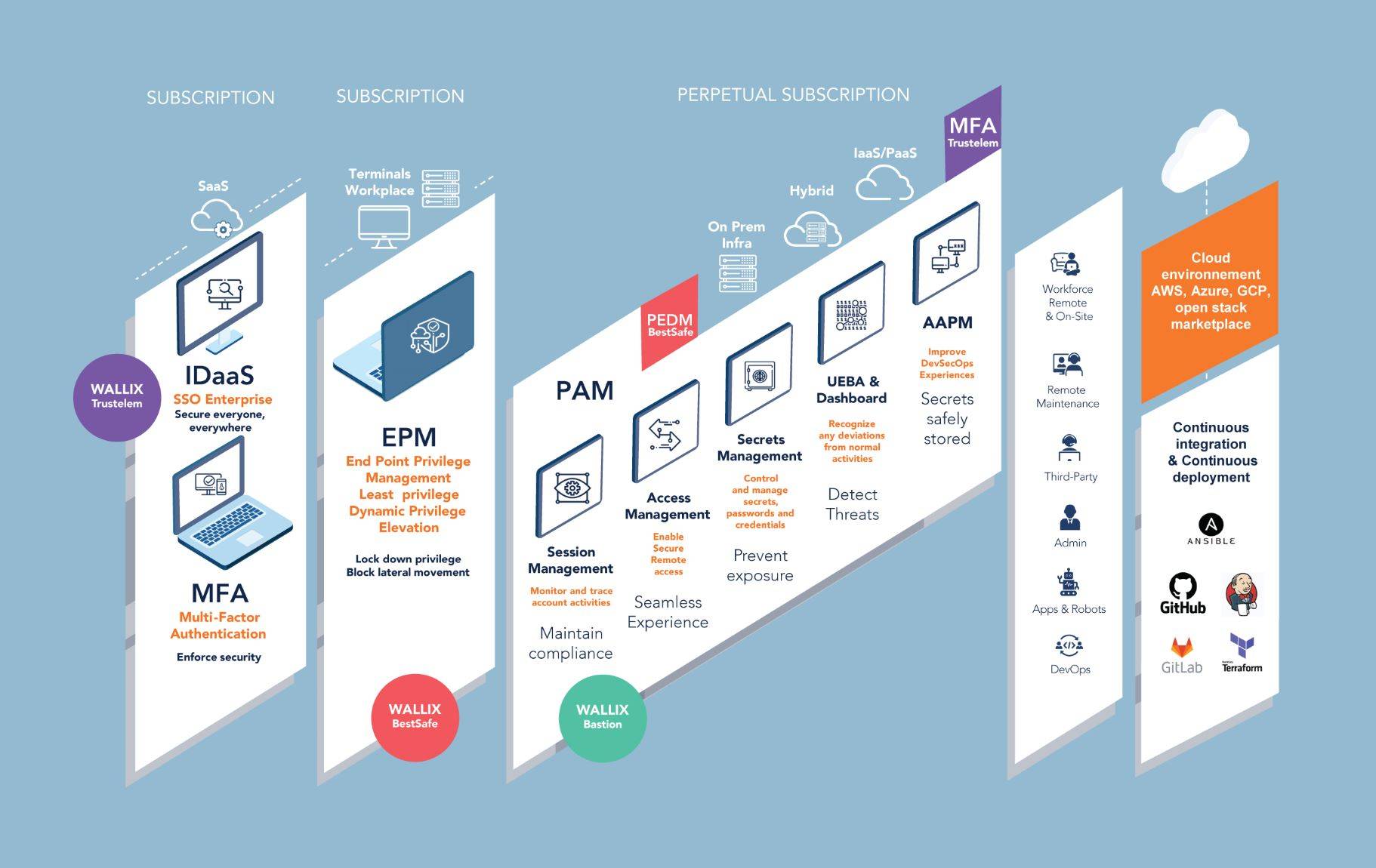
WALLIX PAM4ALL – The Unified Access and Privilege Management Solution
WALLIX PAM4ALL protects, controls, and manages all users’ access to all your assets, for all sessions and for all endpoints, at the right time and from anywhere.
PAM4ALL reduces risks related to access and associated privileges, allows granular management of remote access, and provides access only for specific uses and durations, significantly minimizing the attack surface without affecting productivity and in compliance with regulatory guidelines. Responding to regulatory developments and cybersecurity challenges that affect all businesses, WALLIX solutions protect against cyberthreats, theft, and data leaks linked to stolen credentials and misappropriated privileges.
WALLIX provides solutions to fit in the Zero Trust framework.
Protect your digital future with the leader in simplified access security
Teleworking, cloud computing, and new digital uses are generating an exponential growth in the number of accesses to the information systems of companies. With WALLIX PAM4ALL, the unified privileged management solution, you regain control.
WALLIX protects identities and access to IT infrastructure, applications, and data. Specializing in Privileged Access Management, WALLIX solutions ensure compliance with the latest IT security standards and protect against cyber-attacks, theft, and data leaks linked to stolen credentials and elevated privileges to sensitive company assets. As a leader in the PAM market and with a strategy based on innovation and agility, WALLIX offers a suite of open-ended solutions that are resilient, easy to use, and fast to deploy.
WALLIX Bastion (PAM)
Simplified Privileged Access Management to secure & monitor access from anywhere
Easy to use and easy to deploy, the WALLIX Bastion PAM solution delivers robust security and oversight over privileged access to critical IT infrastructure. Reduce the attack surface and meet regulatory compliance requirements with simplified Privileged Access Management.
Comprehensive Access Security
WALLIX Bastion is a privileged access management software suite (PAM / PEDM) used to manage, control, and trace privileged user access while securing the passwords of IT equipment and infrastructure applications. By applying the principle of least privilege, administrators also no longer necessarily need to have all the privileges on applications, scripts, or processes available on a server to perform a specific task. With the Bastion, you can view users’ sessions in real-time and record their activity for audit or compliance purposes, or to terminate the suspicious activity.
Achieve the highest level of security for on-premise, cloud, and hybrid environments. WALLIX Bastion is also available on Azure and AWS marketplaces.
Session Management
Defend your critical assets from cyber-attack with powerful and easy-to-use Privileged Session Management capabilities. Achieve cybersecurity compliance requirements and monitor privileged session activity, all while increasing IT admins’ productivity and enabling easy control over privileged access. The WALLIX Session Manager offers IT leaders a powerful solution to manage, control, and audit access to network assets with a strong security posture ensuring that only the right person has access to the right IT resources.
Real-Time Monitoring
• Live session sharing enables IT admins to collaborate remotely, participate in training, to monitor system maintenance
• Alerts and automated termination of suspicious activities or unauthorized attempts
• Video recording and replay of all activity including clicks, keystrokes, and command-line while connected to a privileged session to enable powerful search capabilities
Insider Threat & Zero Trust
• Implement a Zero Trust policy with comprehensive session monitoring and management
• Accelerate incident response and analysis with detailed logs and visibility
• Integrate with security platforms, such as SIEM, IDS, and SOAR for deeper analysis
Secure Session Sharing:- WALLIX Bastion’s real-time audit capabilities provide the ability to grant two users access to the same session while guaranteeing the security of the session, as well as providing advanced recording capabilities, and maintaining the confidentiality of sensitive fields like passwords. Bastion users can securely connect from anywhere to receive remote assistance, be trained on advanced and complex systems by an equipment vendor, or to monitor and assist a third-party contractor as they conduct system maintenance.
Password Management
Securely store credentials in a controlled vault and protect passwords against theft and sharing thanks to high-end encryption. Eliminate the use of passwords written on sticky notes or stored in unsecured Excel files, or worse, saved in clear text scripts for all to discover. Leverage high-level password security controls as well as Application-to-Application Password management for tight control over privileged credentials.
The WALLIX Password Manager enables IT leaders to easily control and manage their passwords, secrets, and credentials. It operates with the WALLIX vault or integrates with third-party vaults to protect and enhance existing investments.
Access Manager
Enable secure remote access for IT administrators and external providers to connect safely from anywhere with secure-by-design capabilities; empower your IT team to ensure that only the right person can access the right resource for the right purpose. Eliminate the need to open an RDP, SSH, or Telnet connection thanks to the Access Manager’s HTML5 browser-based connectivity with session management. No additional plugins or fat clients are needed on endpoints, and no untraceable VPN infrastructure to secure access to critical resources.
The WALLIX Access Manager offers advanced multi-Bastion Global Search capabilities for privileged session forensic analysis and can distinguish tenants spanning across several Bastion instances, for a global multi-tenant Privileged Access Management architecture.
Privilege Elevation and Delegation Management
Admin rights can introduce critical vulnerabilities to your vital assets. Ensure that the right privilege is granted to the right user at the right time, without compromising productivity. Privilege Elevation and Delegation Management offers the Least Privilege control over access rights to your most sensitive IT resources. Eliminate overprivileged users and minimize security risks without impeding your teams’ productivity.
Application to Application Password Management
Enable DevOps and Robotic Processes to automatically access critical IT resources in real-time without vulnerable, hard-coded credentials left in scripts. The AAPM module is an easy-to-install software that works with Ansible, Terraform, and other similar tools to allow sealed access to target passwords stored in the WALLIX Bastion Vault.
The WALLIX Application-to-Application Password Manager enables DevOps to access critical resources without ever knowing the credentials. All secrets are safely stored and AAPM enables completely secure access for DevOps tools or robots for unrivaled security and control and unimpacted productivity.
Secure Remote Access
Remote work is increasing in organizations worldwide, creating a need to facilitate secure access to more and more remote users, and making traditional VPN solutions less and less relevant due to their cost and complexity.
Deliver secure remote access to IT admins and external providers via an HTML5-based secure connectivity solution accessible from any browser. Eliminate the need for RDP, SSH, or telnet connections making access to the WALLIX Bastion simple and feature-rich. Remote Sessions benefit from the same level of control, approval, tracking, and monitoring as internal sessions, enabling IT supervisors to control, audit, and analyze all privileged access from anywhere.
Just-In-Time & Zero Standing Privileges
Just-in-Time (JIT) and Zero Standing Privileges policies are the ultimate way to protect IT assets and ensure that the right user has access to the right resources, for the right purpose, and for the right timeframe. Grant privileges only as and when needed to reduce the attack surface, minimize insider threat and implement a robust security policy to protect sensitive IT resources. Provide privileged access to systems only as needed based on the Principle of Least Privilege, no more, no less.
Scalable PAM Made Easy
Experience scalable deployment for the best Total Cost of Ownership (TCO), both on-premise and in the cloud. Deploying a PAM solution is not a one-off project. The WALLIX Bastion is a modular solution enabling organizations to deploy the solution according to macro-level needs, launching features one at a time to facilitate a long-term, sustainable approach to privilege access security. Show results and have the Bastion up and running quickly, and add additional components in a graduated process for ease of change management.
Benefit from significant savings in the short and long term. The WALLIX Bastion’s flexibility and the small number of servers required to run the solution enable IT teams to gain significant savings in administration costs, maintenance costs, and infrastructure costs, making the WALLIX Bastion PAM solution cost-effective at all phases.
Robotic Process Automation (RPA)
Robotic Process Automation (RPA) is increasingly gaining importance in IT and OT organizations. More and more granularity is required to drive Privileged Access Management tools and automate their tasks. With the WALLIX Bastion REST API, users may access any of the features of the Bastion as if they were accessing it from the usual user interface. Any feature available in the traditional GUI is made accessible via an API which gives the robot accessing the Bastion the same level of functionality as any human working on it, including access to secrets and credentials or access to multiple systems.
Powerful Secrets Management
Enforced credential complexity ensures critical systems’ credentials meet strict password criteria
Automated rotation of passwords routinely, after use to stop breaches with shared or hijacked passwords, by account or by domain
An automated restart of services after password rotation of service accounts
Store secrets in a highly secured vault
Eliminate generic Admin and Root passwords shared and used by anyone
AAPM for DevOps & Automation
Secure application-to-application password management
Integrate within Ansible, Terraform, and other similar tools
Secure Robotic Process Automation and Machine-to-machine access security with seal-based AAPM
Eliminate hard-coded passwords in clear text scripts and configuration files for efficient, secure automation
Integrate with industrial systems to enable easy password check-out for connected industrial gateways
You can download the datasheet here.
WALLIX PAM4OT
Secure Remote Access solutions for OT environment
Seamlessly protect critical operations with industry-leading security solutions from WALLIX.
OT.security by WALLIX with its unmatched OT expertise and software certified by the French National Cybersecurity Agency provides purpose-built solutions for industrial control systems, which embrace production constraints while offering optimum security. When it comes to success metrics, production performance can be short-lived if not harnessed by robust cybersecurity. This is why OT.security solutions protect increasingly exposed OT environments without impacting customer industrial and business processes.
Implement Zero Trust Security in OT Environments
Securing industrial operations (Manufacturing):- Secure any protocol, any access, local or remote without adversely impacting the production systems.
When preserving resources is crucial (Critical Infrastructure):- Reduce the risk across critical infrastructure by identifying threats and vulnerabilities, while also providing mitigation strategies.
Protecting sensitive shared or public services from cyber-risk (Smart Infrastructure):- Smart cities improve the quality of life of citizens, but not at any price: cybersecurity solutions mitigate the negative implications associated with cyber-attacks and potential privacy invasion.
For patient data privacy & service continuity (Healthcare):- Improve patient safety and experience and augment efficiency and effectiveness of patient care.
Know more about PAM4OT at https://cloudsdubai.com/products/wallix-pam/ot-security/
WALLIX BestSafe (Endpoint Privilege Management)
Endpoint Privilege Management for powerful Least Privilege security
WALLIX BestSafe is an endpoint privilege solution (EPM) that eliminates the risks associated with overprivileged users and prevents the spread of malware, crypto viruses, and ransomware attacks. WALLIX BestSafe makes it possible to eliminate local administrators on workstations by granting specific rights to each user and distributing privileges to the applications and processes instead of the users themselves. WALLIX BestSafe is the compromise between security and productivity; local nonadministrator users can still execute tasks requiring privileges without the help of IT teams and without jeopardizing the organization’s security.
Innovative Least Privilege Endpoint Security: Eliminate the need for user accounts with elevated permissions thanks to innovative endpoint privilege management. Achieve unparalleled security across all endpoints with permissions controlled at the application and process level – without impacting user productivity.
BestSafe Features
White / Grey / Black Listing
White list for corporate applications, gray list for dangerous applications, blacklist for malware.
> Eliminate privileged accounts and local admin rights
> Grant application-level and process-level privileges to carry out authorized administrative tasks (White list)
> Reduce privileges of potentially dangerous applications (email clients, browsers, etc. with internet access) to deny access to sensitive resources, regardless of user’s elevated privileges (Grey list)
> Stop malware, ransomware, and crypto viruses from executing or encrypting files
Local Group Membership
Take a proactive approach to endpoint security, compared to traditional endpoint management tools, implementing application-level privilege management.
> Eliminate privileges in user accounts
> Manage user-level privileges in addition to application and process privileges
> Assign user accounts to group memberships
> Set time limits for user sessions, automatically terminating the session when the time limit is reached
> Simplify IT administrator workloads
Password Rotation
Put an end to shared passwords used on countless endpoints and tools across local administrator accounts.
> Guarantee each password is unique per computer, account, and day
> Manage password rotation simply and effectively – a given password is only valid on that computer, on that day and time
> Trace attempts to change a password
> Predict future password iterations without connecting to the network
Ransomware Control
Detect encryption attempts in real-time to stop ransomware in its tracks with a near-100% success rate, unlike other technologies
> Automatically detect when a process intends to perform an encryption operation before it is carried out
> Stop the process and execute automated rules for response
> Define rule actions based on standards or administrator thresholds
> Store encryption keys to decrypt at a later date
Application Management
Manage and control all key business applications through an innovative and easy-to-use portal, leveraging BestSafe’s unique process-level privilege management technology.
> Install applications on-demand, or deploy automatically and unattended
> Users perform software installations themselves, without holding administrator privileges or burdening the IT team
> The SDM flexibly and efficiently deploys updates, repairs, admin or maintenance tasks, emergency distributions, and uninstallations, without the need for user interaction or elevated privileges
> Delegate administrative tasks to endpoint users, without granting administrative rights
> Maximize security with no impact on productivity or performance
WALLIX Trustelem (Identity as a Service)
Secure access management to seamlessly connect your workforce to business applications
Simplify and secure access to key business applications from a centralized platform. Protect strategic assets, increase efficiency and productivity, and improve the user experience for both application users and administrators.
WALLIX Trustelem (Identity as a Service – IdaaS) is a service platform to unify, simplify and control user access to any application (administrators and end-users). This solution reduces the risk of cyberattacks by increasing identity and access security and offers efficient administration tools to reduce IT teams’ workload. Service users can easily connect through a customized dashboard, reset their password without requesting the IT team’s assistance, and have the guarantee of secure authentication, appropriate for the nature and type of application being used.
This platform also includes a quick and easy way to limit identity theft and cyber-attacks with a MultiFactor Authentication (MFA) solution. The user access requires several forms of identification to eliminate the risks associated with authentication by password alone (e.g. pin code, fingerprint). It does also deliver access to the specific resources that the user needs, with systematic checking of the requesting user’s identity across the extended scope of the company: internal and external, remote working, and teleworking.
Identity Management Features
Central Directory
Gather your identity sources into a single identity referential to easily control access rights in one centralized location.
> Support for Active Directory, Azure AD, LDAP directories, and Google G Suite directory
> Import as many directories as needed into your WALLIX Trustelem platform
> Complete or partial directory import, based on group membership and attribute filtering
> Import of group memberships and user attributes to define proper access management policies
SSO
Provide users with a Single Sign-On experience to remove the burden of managing a different password for each target application and entering credentials again and again.
> User dashboard displaying all applications to which the user has access rights
> Integrated Windows Authentication and X.509 client certificates support to access the user dashboard with no login form
> Identity federation through SAML, OpenID Connect, and OAuth protocols
> Pre-integrated applications such as Office 365, G Suite, Salesforce, and many others
MFA
Choose from an array of Multi-Factor Authentication mechanisms to fit the specific requirements of your different populations, because there is no one-size-fits-all MFA solution.
> Trustelem Authenticator: a mobile application offering a strong authentication solution that is both secure and easy to use. Within network coverage, Trustelem Authenticator receives push notifications. When the device is offline, the application generates a 6-digit code. In addition to users locking their devices, the application can be fingerprint-protected or require a four-digit PIN.
> OTP over SMS authentication: a simple and practical solution, widely known by users in other contexts
> FIDO 2 security devices: can be used through the WebAuthn protocol to implement multi-factor authentication based on USB or > > NFC physical keys. WALLIX Trustelem supports all FIDO2-compliant devices, including ANSSI-certified devices.
> Google Authenticator or any RFC 6238-compliant OTP generation mobile application is supported by WALLIX Trustelem for multi-factor authentication
Self-Service
Offer users a self-service solution for simplifying and streamlining the management of credentials.
> Active Directory Self-Service Password Reset (SSPR) allows users to re-initialize their Active Directory password independently, after re-authenticating with one or more add-on solutions such as the Trustelem Authenticator mobile app, an SMS, one or more secret questions, a link sent by email, or other solutions
> The user dashboard suggests renewing the Active Directory password either spontaneously or upon expiration
> Users are prompted with MFA enrollment procedures when they access their dashboard or a specific target application so that enrollment is fully autonomous. Administrators control which user or group is prompted for auto-enrollment of the MFA solutions
Straightforward application integration
WALLIX Trustelem has pre-integrated a wide selection of business applications including Office 365, G Suite, Salesforce, Box, Dropbox, OwnCloud and NextCloud, WordPress, and many others to make Trustelem implementation simple. Access detailed documentation for each application for streamlined set-up.
Build quickly, run easily
WALLIX Trustelem is designed to make administration simple and intuitive. The web-based administration console enables IT staff to easily set up directory synchronization, manage life cycles of external user accounts and applications, create and adapt access rules, monitor activity, and audit access security.
Security is your top concern
Keep control over your identities and data! The WALLIX Trustelem platform is hosted and operated by a trusted European cloud provider. Your data sovereignty and security are essential to ensure the quality of service and to protect your company’s assets.
You can download the Whitepaper on The What, How, and Why of Zero Trust Cybersecurity here.