OT Security – Identity & Access Solutions for OT Networks
Seamlessly protect critical operations with industry-leading security solutions from WALLIX
Most OT systems are critical in nature and any downtime can cause severe loss of business. WALLIX is a plug-and-play secure connectivity solution for industrial systems that enables operators to improve compliance and overall data integrity.
PAM4OT
Benefit from global secure access management based on the principle of least privilege.
Increased security posture and governance compliance without complexity. Anchor security efforts in operational resilience to counter the mounting risks by adopting an integrated security strategy focused on identity and access.
PAM4OT is a unified set of state-of-the-art functionalities for securing access and identity in all industrial operations. PAM4OT meets the needs of any industry looking to protect its OT environment through a user-centric approach while providing added benefits beyond security.
It covers industry-specific standards such as ISA/IEC 62443 and the NIST Cybersecurity Framework (especially the Industrial Control Systems requirements of NIST SP800-82). According to the leading analysts (Gartner and Frost & Sullivan), WALLIX offers the best OT Security solution in the market in terms of cost, simplicity, and flexibility.
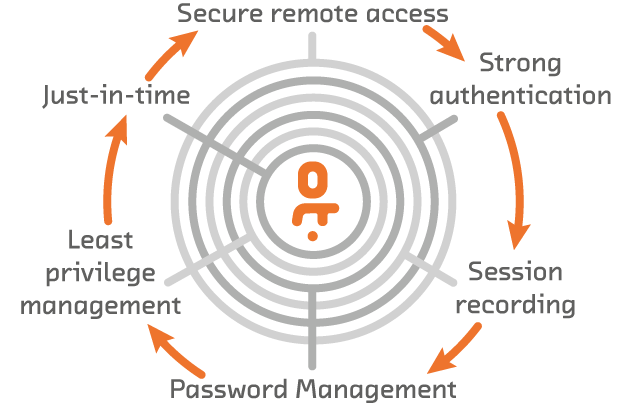
Secure Remote Access: Secure external vendor and admin access to OT assets for maintenance and administration.
Strong Authentication: Strengthen authentication to reduce account takeover.
Just-In-Time: Provide privileged access to systems only as needed.
Session Recording: Defend your critical assets from cyber-attacks with powerful and easy-to-use Privileged Session Management capabilities.
Password Management: Regain control over access to critical OT assets by managing password complexity.
Least Privilege Management: Mitigate the risk of standing privileged access.
OT Security Use Cases
INDUSTRIAL PROTOCOLS: Choose purpose-fit security for real-time production constraints.
WALLIX provides Authentication, traceability, and session control dedicated to OT Security. A unique and proprietary technology from WALLIX of Universal Tunnelling supports all industrial protocols allowing to benefit from the power and simplicity and enhanced user experience. It allows to connect directly to PLCs without going through a bounce server; encapsulating industrial protocols (Modbus, Profinet, S7, EtherCAT, etc.) in an SSH tunnel to ensure the control and traceability of each session. No need for costly bounce servers, as access to resources is granted directly from the usual work environment.
FILE TRANSFER: Enforce control on data and file transfer
WALLIX protects against malicious file uploads. It is recommended to couple the Privilege Access Management tool with an antivirus and provide a dedicated interface for file transfer or transparent copy/paste. Such a solution is offered by PAM4OT offering a cut-off point for IT/OT exchanges.
SERVICE CONTINUITY: Reduce risk and guarantee around-the-clock production
Manage maintenance, repair, and operations without any disruption using WALLIX. PAM4OT is an agentless solution and therefore has no performance impact on the target equipment. The support of the legacy VNC protocol and the associated proprietary overlays allow for a transparent connection to the manufacturer’s supervision stations. No planned downtime is needed to carry out the work to maintenance or repair. Service continuity is never impacted, and the business keeps on running.
REMOTE ACCESS: Seamlessly secure remote access
Get full traceability for internal and external connections. Remote Access allows remote access for remote maintenance workers and maintains both operational efficiency and comprehensive IT-OT security. PAM4OT provides a VPN-less secure external user connection to facilitate software upgrades, periodic maintenance, or any support activity within OT networks.
Embrace the ever-expanding dimension of complexity
Digitalization and the Fourth Industrial Revolution pose new challenges and call for innovative solutions.
OT systems were not initially designed to be secure, which makes them particularly vulnerable to cyber threats. Any compromise of industrial control systems can be extremely serious resulting in downtime, loss of production, health and safety risks, and environmental impacts.
Today, access and identity are consumed by a wide range of stakeholders within and outside the company which proportionally increases the attack surface exposing all company resources to cyber threats. Everything from physical infrastructure to devices and applications becomes vulnerable, further weakened by enterprise mobility and collaboration trends. “Stakeholder management” is inevitably driving the adoption of Identity and Access Management (IAM) technologies.
OT Security by WALLIX with its unmatched OT expertise and software certified by the French National Cybersecurity Agency provides purpose-built solutions for industrial control systems, which embrace production constraints while offering optimum security.
When it comes to success metrics, production performance can be short-lived if not harnessed by robust cybersecurity.
This is why OT Security solutions protect the increasingly exposed OT environment without impacting customer industrial and business processes.
WALLIX solutions have been designed in a way that takes into account users and processes, production needs and global constraints, sectoral imperatives, and safety issues. OT Security solutions foster fluid workflows for cyber secure identity and access to OT environment in all sectors: manufacturing, healthcare, smart and critical infrastructure
Key benefits of OT Security
> Simplify Operations
> Guarantee Availability
> Maintain Productivity
> Eliminate Risk
> Address Compliance
Implement Zero Trust Security with OT Security
Manufacturing – Secure Industrial Operations: Secure any protocol, any access, local or remote without adversely impacting the production systems.
Critical Infrastructure – When preserving resources is crucial: Reduce the risk across critical infrastructure by identifying threats and vulnerabilities and providing mitigation strategies.
Smart Infrastructure – Protecting sensitive shared or public services from cyber risk: Smart cities improve the quality of life of citizens, but not at any price: cybersecurity solutions mitigate the negative implications associated with cyber-attacks and potential privacy invasion.
Healthcare – For patient data privacy & service continuity: Improve patient safety and experience and augment efficiency and effectiveness of patient care.