VAPT Services: Cost-Effective & Best Penetration Testing in UAE
What is Penetration Testing or VAPT?

VAPT Testing Methodology

Information Gathering
All our VAPT security testing assessments start with information gathering. We use the Open-source intelligence (OSINT) framework to collect data from publicly available sources to be used in an intelligence context. With information gathering, a lot of actionable and predictive intelligence can be obtained from public, open-source, and unclassified sources.
Enumeration
This process begins with detailed scanning and research into the architecture and environment, to discover potential attack vectors in the system, and the same can be used for further exploitation of the system.


Automated Testing
Once the target has been fully enumerated, we use vulnerability scanning tools and manual analysis to identify security flaws. With vast experience, in-depth technical knowledge, and custom-built tools, our security engineers find weaknesses most automated scanners generally miss.
Exploration and Verification
At this assessment stage, our consultants review all previous data to identify and safely exploit identified application vulnerabilities. Once sensitive access has been obtained, the focus turns to escalation and movement to identify technical risk and total business impact. During each phase, we keep client stakeholders informed of testing progress, ensuring asset safety and stability.


Privilege Escalation
Once a vulnerability is exploited, the privilege accrued through the exploitation is further exploited to gain higher privilege or escalate the access level. Privilege escalation demonstrates real-world threats and attacks to systems in scope and other systems on the connected network.
Assessment Reporting
Once the VAPT engagement is complete, a detailed analysis and threat report, including remediation steps, is developed. We provide clear and concise reports, prioritizing the highest-risk vulnerabilities first along with detailed mitigation recommendations.


Retesting
After the remediation, we provide one free retest of the target to validate the effectiveness of remediation. We will provide an updated VAPT testing report with a new risk level.
Web Application / Website Penetration Testing
Web Application Penetration Testing tests the vulnerabilities of web applications, specifically for application-related vulnerabilities. Our web app penetration testers use automated and manual techniques to identify security vulnerabilities in the application that could allow the disclosure of sensitive information or the disruption of services by outside attackers. The tester uses a comprehensive web app penetration testing methodology that identifies security vulnerabilities from the OWASP Top 10, OSSTMM, and PTES and security vulnerabilities that are specific to the application. Web app pentest can be done with credentials or without using the same.
Website penetration testing
Helps you identify and fix security flaws on your website. Website Pen Test also evaluates misconfigured integrations implemented within a website.
Desktop Application Penetration Testing
Helps you to identify security issues within the desktop application. Tests include injections, authentication bypass, session management, file uploads, & review of data communications.
Web Services / API VAPT
An API pen test imitates an attacker specifically targeting a custom set of API endpoints and attempting to undermine the security. Our team will follow an assessment according to our API penetration testing methodology. Our pentester will use a comprehensive testing methodology which will identify security vulnerabilities from the OWASP Top 10 as well as security vulnerabilities that are specific to the API itself.
Metaverse Penetration Testing
Involves assessing the security of virtual environments and interconnected digital spaces. We explore user interactions, communication channels, and data exchanges to identify vulnerabilities such as injection attacks, authentication bypasses, and privilege escalation. Evaluate the security measures for users’ virtual identities, data privacy, and authentication mechanisms.
We check for the following among others during the Web Application VA/PT exercise:
Mobile Application Penetration Testing
Mobile Applications VAPT can be done for Android or iOS applications. Our approach to mobile app pentest will make use of dynamic and static analysis to test all accessible features within the mobile application. Our testing approach will use a virtual machine (Android) and physical phones that are jailbroken or rooted (iOS and Android). This helps us cover all features using automated analysis as well as manual testing within the scope. The testing will be based on the OWASP – Mobile Security Testing Guide (MSTG). The vulnerability report will be based on the OWASP Mobile Top 10.
Testing coverage for data security at rest
Investigate using a malicious application, if the data can be accessed or recovered across applications and the cross-application boundary is secure, and identify if the application exposes any Personally Identifiable Information (PII), API keys, passwords, or any other application contextual sensitive data, verify that any sensitive content stored locally is encrypted, Applications are resilient to reverse engineering and tampering attacks.

Testing coverage for data security in transit
Test that multi-factor authentication cannot be bypassed, or brute-forced, usage of strong encryption, inter-application redirects are secure and cannot be tampered with, session hijacking, client-side security, hidden URL schemes exposing access to development environments, application hooking and run time manipulation, bypass any application restrictions, such as features that are shipped but disabled, review code for hardcoded secrets.

Client-Side – Static and Dynamic Analysis
Tests include reverse engineering the application code, hard-coded credentials on source code, insecure version of Android OS installation, cryptographic-based storage strength, poor key management process, use of custom encryption protocols, unrestricted backup file, unencrypted database files, insecure shared storage, insecure application data storage, information disclosure through Logcat/Apple System Log (ASL), URL Caching on cache.db, keyboard press caching, copy/paste buffer caching, remember credentials functionality, client-side based authentication flaws, client-side authorization breaches, insufficient WebView hardening (XSS), content providers: SQL Injection and local file inclusion, injection, local file inclusion through NSFileManager or Webviews, abusing android components through IPC intents, abusing URL schemes, unauthorized code modification, debug the application behavior through runtime analysis.

Server-Side – Web Services/API Calls
Bypass SSL pining, Excessive port opened at the firewall, default credentials on the application server, service catalog, exposure of web services through WSDL document, security misconfiguration on Webserver, input validation on API, information exposure through API response message, bypassing business logic flaws, session invalidation on the backend, session timeout protection, cookie rotation, token creation.




Network VAPT
During Network Penetration Testing, we simulate an attack on the client’s system or network. Using popular pen testing tools, proprietary scripts, and manual testing, we do our best to penetrate the network without harming it during the pentest exercise. After the pen-testing exercise, our pen testers point out the flaws in the client’s network along with mitigation advice to fix the same. This helps the client improve infrastructure, configuration, and processes to strengthen security. Network Penetration Testing can be done as an onsite or offsite assignment.
The penetration test begins by first identifying the scope of the engagement, including the IP addresses or hostnames of any servers and hosts that are in scope for the assessment – the client will provide this information prior to the commencement of testing. The client will also provide the tester with an external IP address to the DMZ network.
Vulnerabilities will then be identified in the external and internal environment of the client. These vulnerabilities may be exploited to validate the vulnerabilities and expand access over the affected system. Finally, the information gained from the access will be fed back into the previous phases to determine if any additional vulnerabilities can be identified. In the simulation of a real-life attack, access gained by compromising any affected systems may be used to pivot to other systems in the internal network.
The following components are analyzed during a VA PT testing exercise :
Penetration Testing Scope
A penetration test is a method of evaluating the security of a computer system or network by simulating an attack from the internet. The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known and unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. This analysis is carried out from the position of a potential attacker and can involve the active exploitation of security vulnerabilities. Any security issues that are found will be presented to the system owner together with an assessment of their impact and often with a proposal for mitigation or a technical solution. The intent of a penetration test is to determine the feasibility of an attack and the amount of business impact of a successful exploit if discovered.
Involves risk analysis of the IT components behind the classic firewall infrastructure. All network components including servers, workstations, network devices, VPN, and MPLS are subjected to a detailed analysis during this network pen testing exercise. During External Penetration Testing, security vulnerabilities with Public IPs, Firewalls, DMZ, and Web Applications are identified that hackers could exploit. External risk analysis begins with a detailed reconnaissance phase to understand the security measures in place. VAPT testing covers the below scope
Our Security Consultants will use the industry’s best tools, vulnerability scanners, methodologies, and custom scripts and tools to conduct a thorough vulnerability analysis on the target systems and report them based on severity.
The results of the vulnerability identification are paired with their expert knowledge and experience, to conduct a manual security analysis of the target systems finally. Our assessors attempt to exploit and gain remote unauthorized access to data and systems. Tests will also be conducted to determine if these exploits could be escalated in any possible ways using social engineering techniques to escalate to higher privilege or other directly connected systems with higher trust levels using privilege escalation techniques.

Penetration Testing Report
VAPT Report will have a detailed list of the identified vulnerabilities rated as critical, high, medium, and low risks to determine the impact, likelihood, and overall risk that the vulnerability presents. The risk factors include:
- The business context of the vulnerability, including whether an attacker could gain access to sensitive information, or could impact the operation of the business
- The technical context of the vulnerability, including whether an attacker could use this vulnerability to gain further access to the environment, exploit other vulnerabilities, or access other systems
- The technical ability required to exploit the vulnerability
- Any mitigating factors that could prevent or limit the successful exploitation of the vulnerability.
How much does penetration testing cost?
Penetration test pricing depends on the type of VAPT testing. Network penetration testing services prices depend on the number of assets covered during the pen test. Web Application penetration testing services cost is calculated based on the type of test conducted (Black box or Grey box or White box) and the number of web applications. Mobile Application pen test pricing depends on the number of applications and mobile platform. The same mobile applications in Android and iOS are considered two separate applications for calculating pen test costs. External penetration testing cost is calculated based on the number of Public IPs and applications.
Types of Penetration Testing (VAPT)
Our Vulnerability Assessment and Penetration Testing evaluate the target security control’s ability to block or prevent attacks. VAPT services can be conducted in 3 ways to simulate different attack scenarios under internal & external penetration testing services.
Continuous Pen Testing is recommended for Web and Mobile applications to identify security gaps before a hacker does. PenTesting services at regular intervals help you to maintain and improve your application’s security posture. Configuration Review evaluates the configuration of critical devices of your IT network including Servers, Firewalls, and other networking devices to analyze the security effectiveness of the IT environment. It ensures that your network meets current security standards and policies.
Pen Testing Tools
We use multiple tools for VAPT services, which include commercial, open-source tools and custom scripts. VA and PT rely extensively on manual testing and verification of each potential vulnerability identified by various tools. We use the Security Vulnerability Scanners & Metasploit framework to scan for common security issues and misconfigurations. Pentest Tools will be configured with the latest updates from the professional feed. The scanner may run throughout the testing period whilst the auditor is manually testing for other vulnerabilities.
Frequently used tools for VAPT testing
- Nessus, Core Impact, Qualys, Burp Suite
- Metasploit, ZAP, Sqlmap, Nmap
- Acunetix, Net Sparker, DIRB, Nikto
- Nipper, Wireshark /Tcpdump, Fiddler
- Brutus, SSLDigger, Hydra, MobSF, QARK
- Scout Suite, Prowler, AWS Security Benchmarks
- Commix, Mutiny, Boofuzz, Kitty
- Firmware Analysis Toolkit, Fwanalyzer, ByteSweep
- Firmwalker, Binwalk, QEMU, Firmadyne
- Flashrom, Minicom, Prelink, lddtree
We use many more tools, and scripts that are apt for the target and scope for VAPT testing in Dubai UAE, and the Middle East. Our Cybersecurity experts comprise a pool of highly qualified and skilled professionals with experience in handling complex and demanding requirements from a diverse set of clients in the UAE. We have carried out more than 600+ pen tests in Dubai UAE and our Pen Testers have vast experience in various industry verticals such as Banking, Insurance, Money Exchange, Oil & Gas, Government, Retail, Hotels, Manufacturing, Telecom, Healthcare, Construction, E-commerce, Education, etc. with certifications in specialized areas such as CISSP, OSCP, OSWE, CSX-P, CISA, CEH, etc.

Benefits of Penetration Testing
Penetration testing plays a significant role in an organization’s security strategy. It helps organizations proactively identify vulnerabilities before attackers can exploit them. It helps companies to protect their assets and data. VAPT helps to identify and fix the security gaps in an organization arising due to outdated software or configuration flaws. It also helps to improve the overall security posture of the organization. Penetration testing helps organizations meet compliance requirements as many regulatory frameworks require regular penetration testing to ensure that sensitive information is adequately protected.
Source Code Review can also be done as part of the VAPT testing exercise to verify the security of the source code of your application.
You can download the VAPT case study here.
Vulnerability ScanEngine
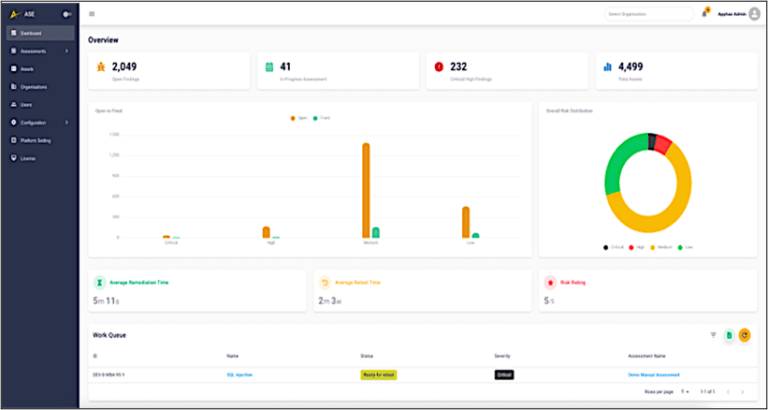
Unleash the power of unlimited automated Vulnerability Assessment scans, both authenticated and unauthenticated, with ScanEngine. Our cutting-edge platform offers a comprehensive solution for all your security needs. With ScanEngine, you gain access to a wide range of features designed to enhance your vulnerability assessment capabilities. Our platform comes with industry-leading tools such as Nessus Professional and BurpSuite Professional as part of the platform, providing you with unrivaled scanning accuracy and efficiency.
ScanEngine empowers you to take control of your assets from a single, centralized platform. Effortlessly manage and monitor your entire network, whether it’s internal or on-premises, using our innovative virtual appliance technology. Now you can proactively identify vulnerabilities, pinpoint risks, and ensure the security of your entire infrastructure with ease. you have the power to automate your vulnerability assessments. Set up periodic scans to run at your preferred intervals and receive automated reports directly to your inbox.
The platform allows you to tailor your reporting content according to your specific requirements. Showcase the information that matters most to you, presenting it in a clear and concise format that aligns with your organization’s needs.
Perform VAPT at Scale
Customers can quickly initiate their assessments, keep track of their vulnerabilities, and take faster actions to remedy vulnerabilities from the ScanEngine platform.
- Vulnerability Management: Manages the lifecycle of vulnerabilities from identification to remediation which helps organizations with faster remediation timeframes.
- Automated Scanning: Perform intelligent automated scanning on your infrastructure and applications seamlessly.
- Penetration Testing: Manage your penetration testing activities from a single pane of the console to track your vulnerabilities and on-the-go report
- Asset Management: ScanEngine automates vulnerability scans of your assets to provide an in-depth view of vulnerabilities with guided remediation.
- Enhanced Reporting: Generate your PDF and Word reports on the go as you demand. Access the full penetration testing reports from the platform with an executive summary, high-level analysis, and detailed vulnerabilities.

Frequently Asked Questions
Typically, professional assessments range from AED 15,000 to AED 150,000 based on scope.
A standard engagement takes 5 to 14 business days, including testing, reporting, and integration with SOC services for ongoing monitoring.
Yes, Clouds Dubai is an ISO 27001 certified organization specializing in UAE compliance.