Your search for the most secure and cost-effective MFA solution ends here! inWebo MFA solution offers the highest security on the market thanks to the unique combination of random dynamic key technology and HSM (Hardware Security Module). Accessible in SaaS, rich in connectors, APIs, and SDKs, inWebo MFA (or 2FA) adapt to your technical constraints without imposing new ones. Streamline the connection experience of your users and benefit from the many advantages of the MFA solution.
Most cyber-attacks originate from the theft and fraudulent use of identification data. Multi-factor authentication is an effective countermeasure as long as the level of security offered by the solution is not compromised. inWebo is constantly innovating to ensure the highest level of security without compromising the user experience or the ease of integration and deployment.

It can be integrated into all your SaaS applications, VPN access solutions, Privileged Accounts (PAM), Single Sign-On (SSO), Identity and Access Management (IAM), and even from the design stage of your applications. inWebo’s multifactor authentication solution meets your authentication needs and protects your resources with flexible integration modes that can be adapted to the specific context of each need. Prevent common attacks that bypass typical 2 FA solutions like Man-in-the-middle attacks, Man-in-the-endpoint attacks, stealing of passcode generators & 2FA brute force attacks using inWebo’s unique random dynamic key technology.
Clouds Dubai offers the UAE with inWebo’s highly secure MFA, the most secure and cost-effective solution on the market. It uses a unique random dynamic key technology that makes it compatible with your technical constraints without the need for the logistical costs or physical key management of hardware tokens. This ready to use solution has already supported numerous organizations across the UAE in tackling regulatory issues and adhering to auditing requirements while providing Phishing-resistant MFA to stop Man-in-the-middle attacks.
Investing in cybersecurity means contributing to the agility and flexibility of the organization to optimize its operations.

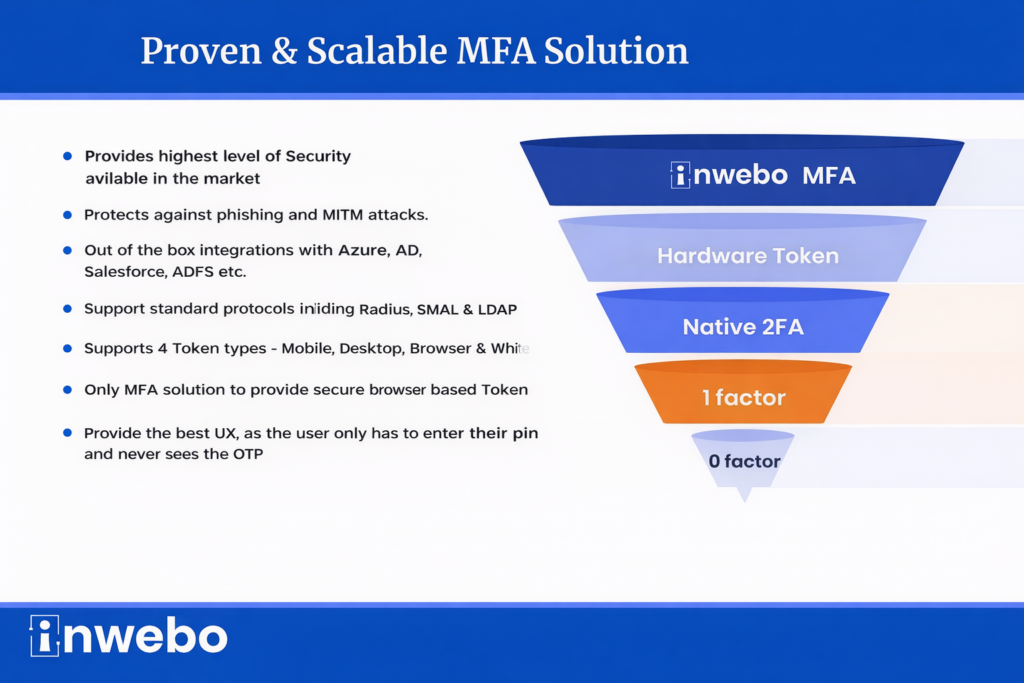
According to your needs, you can use inWebo MFA to add a security layer to existing application passwords, to replace them entirely, to combine biometric authentication along with any token authentication, or even to limit the number of authorized tokens.

inWebo helps you to meet the challenge of managing strong authentication on networks of several thousand users. This involves integration, testing, provisioning, embedding, user support, administration, auditing, usage data analysis…
We make sure that all of these areas are fully covered in the solution. Thanks to the programming interface (API) and development kit (SDK), you can execute them from existing tools at any time. Provisioning and integration are supported by your identity management platform.
The IWDS tool (inWebo Directory Sync) is designed to help you synchronize users, groups, and processes within your inWebo account. Integrated and customizable tools will help you deploy our solution to all your users without having to create a workflow. The authentication tools are available for download and can be customized with your branding.
With the arrival of the PSD2 in Europe, ensuring the security of transactions is becoming a regulatory issue for all commercial and financial players. inWebo provides a transaction sealing solution that establishes a dynamic link between the transaction, the amount, and the beneficiary. Therefore, the transaction becomes unreputable.
InWebo’s strong authentication solution can be integrated with Microsoft’s cloud-based identity and access management service (Azure AD). With fast and easy integration and deployment, you can benefit from the combination of enhanced security and a seamless user experience.
Azure AD users can now benefit from the solution, a key element in the implementation of a “Zero Trust” security
model based on the principle of “verify and never trust”. inWebo brings to access control in Microsoft’s cloud environment a level of security higher than the one provided by any other software token solution, without the constraints of a physical, hardware token (physical key management, logistics, costs of implementation).
Azure AD integration is now essential for companies that rely on Office 365 and Microsoft cloud identity management. inWebo offers a flexible MFA solution to secure all applications within the Microsoft Cloud, with the benefit that it can also be implemented in any other application that is open to internal users (employees) or external users (partners and customers).
Many fraudulent attacks target the accesses of your customers, employees, or partners. Multifactor authentication (or 2FA) offers complete protection against the below attacks.

91% of cyber attacks begin with phishing with dramatic consequences: theft of confidential information, fraudulent transfers, impact on the company’s brand image, etc. MFA makes sure that only genuine users can gain access.

The increase in identity data leakage and the tendency for users to use the same passwords on different services are fueling the strong growth in credential stuffing attacks (30 billion reported by Akamai in 2018). Multifactor authentication adds one more layer to the password thus protecting users.

The discreet installation of malware (keyloggers) on users’ computers allows hackers to retrieve credentials to spoof accounts and identities. MFA makes leaked passwords useless for cybercriminals.
Protect your resources from phishing, credential stuffing, and ransomware with a solution that adapts to your technical constraints without imposing new ones.
Copyright © 2026 Clouds Dubai, Powered by Oktohut