InDefend provides Data Loss Prevention (DLP), Insider Threat Management, User & Entity Behavior Analytics (UEBA), and Employee Productivity Monitoring. It includes tools for monitoring employee activities, detecting anomalies, preventing data theft, and improving organizational productivity.
InDefend Data Leakage Prevention solutions use behavior analytics and employee monitoring to prevent data leakage and insider threats. InDefend is a data loss prevention solution that minimizes the loss and theft of critical business data through customized access policies by providing a real-time feed of data that’s been sent out on a daily basis. It creates a controlled environment for information outflow on various channels and portable devices. InDefend’s Intelligence reports give proactive warnings about probable data loss through notifications, alerts, SMS, and emails to identify and block sensitive data from leakage.
The data loss prevention application is designed to prevent access to unauthorized removable media devices, websites, and applications. All monitoring and control are done directly at the endpoint level, thus reducing the cost of implementation and usage. The cloud-based deployment of the indefent data leakage prevention solution allows monitoring and control, anytime and anywhere. This provides a wider scope of monitoring and analytics capabilities to offer greater benefits than traditional DLP solutions. inDefend also provides offline control and monitoring for computers disconnected from the organization network. It can handle bypass scenarios of the data card, onion routing, tunneling, etc. effectively. It also monitors data leaks from messengers, skype sessions, G-Talk, etc.
inDefend data loss prevention solutions combine Fraud Analytics, Data Leakage Prevention, and forensics with the integrated dashboard. indefent can be deployed and configured with minimal time and provides the maximum ROI compared to traditional Data Leakage Prevention solutions.

Protect your confidential data from being compromised by your own employees and gain maximum insights.

Monitor and improve the productivity of your employees by keeping track of work activities and work hours.

Gain access to insightful user data that can help you understand an employee’s organizational behavior.




A daily update on data feed of what is being sent out and by whom to prevent data loss
Stay informed about probable data loss through desktops notifications, SMS alerts, and email reports
Collect corporate information going out on various channels and portable devices. Maintain a record of employee activity on a daily basis
Identify and block sensitive corporate data right at the point of origin and save millions of dollars
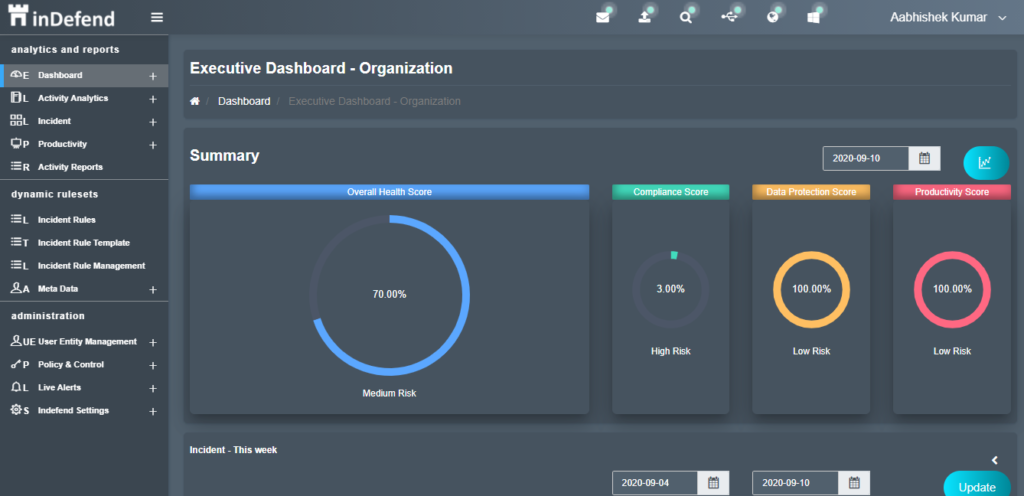
Reporting for the management on incident reports of Data Loss, Sensitive Online Search Activities and Internet Bandwidth Loss, etc. based on the data gathered by inDefend
Monitor and restrict access to sensitive websites using real-time URL classification
Enforce end-users to copy data to removable storage devices in a hidden, password-protected, and encrypted vault
Periodic screenshots of end-users desktop activities
This data loss prevention feature stores the exact copy of the outgoing mail with inDefend
This includes Application Sandboxing, Daily Email Reports, covering incident alert, summary and any change request alert, Search Activity Monitoring, Whitelisting & Granual control of USB Devices, USB Storage Encrypted Container, Data Discovery and Data at Rest Scan
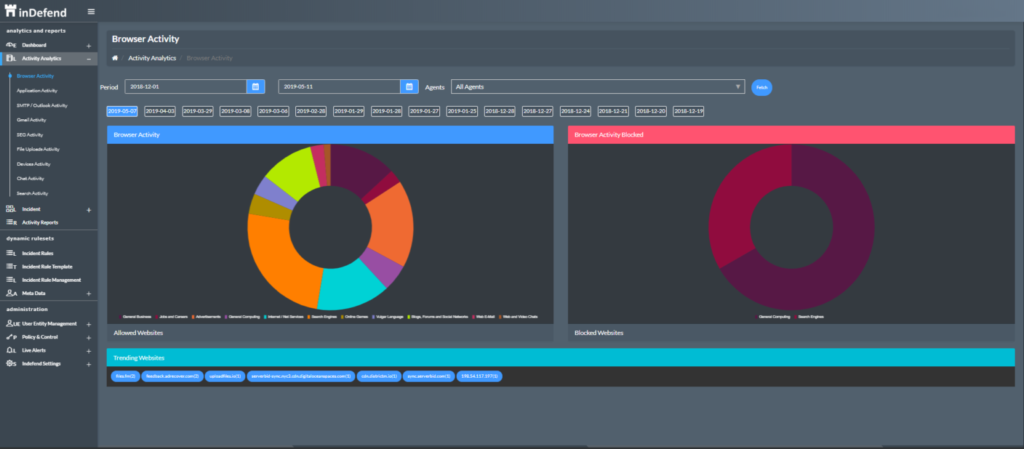
inDefend addresses various challenges related to insider threats with integrated software with Employee Behavioral and Productivity Monitoring, Application Monitoring, Browser Monitoring, Device Control & Data Leakage Prevention. inDefend provides a detailed analysis of network apps, web file uploads, external media devices, email, and browsing activity.
It monitors emails, applications, file uploads, website access, removable media transfers & device control by analyzing chat, search activity, email, file uploads, browsing activity, and application activity. inDefend also provides Screenshot Monitoring & Shadow Logging.



inDefend provide Industry’s True UEBA with DLP which focuses on providing an end-to-end solution for Insider threats and data-leak covering a unique combination of Data leak prevention solutions, Compliance, and Governance with a proactive approach from a single solution. This unique concept offers single client single server architecture and has an inbuilt database and data classification feature, which means the customer doesn’t need to worry about relying on different vendors.
Also, it is one of the unique offerings which have an integrated solution covering user monitoring, device control, behavior analysis, DLP, Reporting, and Analytics from a single Console. The policy resides at the endpoint which makes it easy for the security team while monitoring & controlling any endpoint either online, offline or remote in real-time.
inDefend is designed to secure an enterprise workforce that detects anomalous employee behavior as opposed to their regular behavioral patterns. inDefend Threat Detection Modules are given below.
InDefend is built to achieve full transparency over all the computers of the organization by maintaining relevant data and network control. The application is designed to prevent access to unauthorized removable media devices, websites, and applications.
Secure Email Gateway (SEG) enables a secured approach for the sensitive content going through the corporate email channel to any third party, via an agentless approach. SEG is empowered to provide you with the capability to monitor and block outgoing emails through a gateway-based approach.
Secure Printer Gateway (SPG) is created to prevent potential data leakage from printer gateways. Regulate access to the printing of documents within the corporate environment to prevent unauthorized access, misuse, and theft of critical documents.
With inDefend-SAM, a comprehensive solution to track various activities performed by administrators after logging onto such servers, organizations can now feel comfortable by adding one more layer of security, auditing and surveillance on their critical IT infrastructural assets.
Copyright © 2026 Clouds Dubai, Powered by Oktohut