BluSync is a hybrid file sharing and collaboration application for the agile enterprise. With military-grade security and privacy, BluSync puts innovation and productivity on the fast track without the worry about where employees store their digital assets.
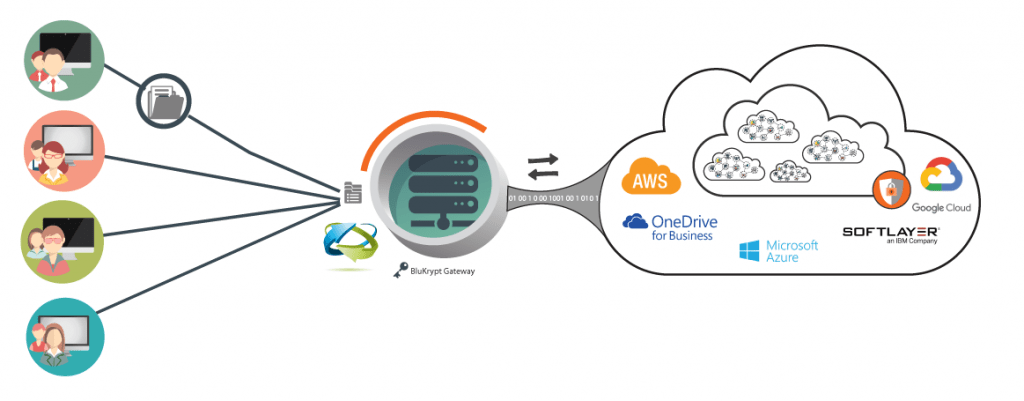
BluSync Secure File Sync enables your employees to collaborate seamlessly among themselves and also with external parties across locations, while allowing access across multiple devices, so business gets done on the go. It supports a concept called mini-clouds, allowing groups of users to collaborate effectively. It leverages BluKrypt™ – unique storage container technology – to make the solution unmatched in terms of security, privacy, and control when deployed in a public or hybrid cloud configurations. BluSync Secure File Sync is cloud/storage agnostic and works with several popular cloud storage providers seamlessly.
BluSync SEcure File Sync & Share helps businesses connect people with processes and data in an easy and secure way.
It is an Enterprise Secure File Sync & Share solution. It is a secure platform for teams to access, edit, and share files in a fast and efficient way. With BluSync Secure File Sync, team members can connect to content in the enterprise cloud, or mini-clouds, and access the information therein securely. It maintains an auditable trail of activities that takes place in the cloud environment, helping organizations retain full and complete control and visibility into the way content collaboration and file sharing happens.
Easy sharing anytime, anywhere. Sharing a file with a colleague or someone outside your organization is literally just a click away. BluSync generates a link that you can copy in to an email to send, or will even send the email for you. Worried that the link may end up in the wrong hands? No problem. Parablu gives you policy-based sharing with password protection, read-only access, and even allows the expiration of document links.
SecureFTP based home-grown solutions held together with scripts can be a thing of the past. Whether it is sharing a single file or ongoing collaboration – BluSync handles it effortlessly. You can automate business processes by having files deposited into pre-determined locations. BluSync will know to auto-share / route the file to the right collaborators based on the folder it is placed in.

Copyright © 2026 Clouds Dubai, Powered by Oktohut
Active Directory penetration testing requires a comprehensive and engaging methodology to identify vulnerabilities, assess risks, and strengthen the security of Active Directory.
Cloud PenTesting assesses the weaknesses and strengths of your public and private instances with cloud computing platforms like AWS, Azure, GCP & more. It assesses Azure Active Directory, Amazon Web Services workloads, serverless functions, or Kubernetes to ensure that your cloud networks are safe and secure. Cloud penetration testing examines the security of cloud applications, configurations, passwords, encryption, APIs, databases, and storage access. The total number of cloud accounts and instances determines the cost of AWS Penetration Testing & Azure Penetration Testing.
We assess the security configurations against industry best practices such as SANS CIS benchmarking, NIST, and PTES. The following list is a summary of the primary security controls assessed for Cloud PenTest.
Configuration review is done for critical infrastructure devices like Firewalls, Switches, and servers to analyze the current configuration, looking for security gaps or vulnerabilities from both a best practice perspective as well as a realistic risk perspective. The configuration review is performed using either offline configuration review which includes the offline configuration script review to identify security flaws in the network device configuration files or using credential review where an authenticated agent will try to identify the configuration flaws in the network devices.
Firewall VA PT evaluates the security of the Firewall using the security audit to identify vulnerabilities in the Firewall. The results of the firewall pen testing will help the organization enhance the security of its Network Firewall. Firewall pen-testing involves port scanning, banner grabbing, ACL enumeration, Firewall architecture and policy review, port redirection, internal and external testing, HTTP tunneling, firmware review, etc.
OT system is fundamentally different from an IT system. It requires specific controls that would not impede its availability, integrity, and confidentiality. Standards such as ISO27001/22, NERC- CIP, NIST, and IEC62443 can be used collectively when evaluating the security posture of an OT system. OT Pen Testing is done on PLCs and Embedded Controllers, HMIs and SCADA systems, Networking equipment, Switches, Routers, and Security appliances.
Performing the vulnerability assessment on OT systems involves:
IoT Pen Testing looks for security vulnerabilities in Internet of Things devices and networks like cameras, thermostats, smart locks, industrial control systems, medical devices, etc. IoT Pen Testing helps to identify and assess the potential risks and threats posed to the data, device & network. This includes vulnerability testing for unsecured passwords, encryption, and other weaknesses that malicious actors could exploit. IoT VAPT methodology consists of nine stages tailored to conduct firmware/IoT security assessments.