
Executive Summary
Cloud adoption across the UAE has moved past experimentation. Enterprises are now running critical workloads across multiple cloud platforms, blending public cloud, private cloud, and on-prem environments. This shift delivers speed and flexibility but it also introduces complex, compounded security risks that traditional security models cannot handle.
By 2026, Cloud Security UAE will no longer be just an IT concern. It will be a board-level risk, directly tied to data protection, regulatory exposure, business continuity, and brand trust.
This guide explains:
- What cloud security means in the local UAE business and regulatory context
- Why multi-cloud environments are harder to secure
- The key cloud security trends shaping 2026
- A practical, architecture-driven approach to securing multi-cloud environments
- A clear 90-day execution plan for UAE enterprises
If you are responsible for cloud strategy, security, or compliance in the UAE, this article is designed to help you move from tool sprawl and uncertainty to clarity, control, and confidence.
1. Why Cloud Security Is a Board-Level Issue in the UAE (2026 Context)
UAE organizations are under increasing pressure to modernize. Digital transformation, smart government initiatives, remote work, AI adoption, and regional expansion have all accelerated cloud usage.
At the same time, three realities have changed the risk equation:
- Data is distributed across clouds, regions, and services
- Identity has replaced the network perimeter
- Regulatory scrutiny is rising, especially around sensitive and personal data
In a multi-cloud environment, a single misconfiguration, excessive permissions, or blind spot can expose data across the entire organization.
For UAE enterprises, weak cloud security practices can lead to:
practices can lead to:
- Regulatory penalties and audit failures
- Loss of trust from customers and partners
- Operational disruption across borders
- Reputational damage that is difficult to reverse
This is why cloud security in the UAE in 2026 must be treated as a business resilience strategy, not just a technical implementation.
2. What Multi-Cloud Security Really Means (Not the Marketing Definition)
Multi-cloud security is often misunderstood.
It does not mean:
- Buying separate security tools for each cloud
- Applying the same on-prem security controls in the cloud
- Relying entirely on the default cloud provider protections
In practical terms, multi-cloud security means:
Maintaining consistent visibility, control, and protection across all cloud platforms, workloads, identities, and data without gaps or contradictions.
Multi-cloud vs hybrid cloud
- Hybrid cloud blends on-prem and cloud environments
- Multi-cloud involves multiple cloud providers, often with different architectures and security models
Both increase complexity but multi-cloud introduces policy fragmentation, identity sprawl, and data exposure risks if not handled correctly.
One of the biggest challenges in cloud security initiatives in the UAE is assuming that securing each cloud individually equals securing the environment as a whole.
3. Cloud Security Trends Shaping 2026
3.1 Security platforms replace isolated tools
Organizations are moving away from fragmented point solutions toward integrated platforms that support Cloud Security UAE goals across posture management, workload protection, identity risk, and runtime monitoring.
Why it matters:
Disconnected tools create blind spots. Integration reduces risk and improves response time.
3.2 Identity becomes the primary attack surface
Attackers target identities because they bypass traditional defenses.
In 2026, effective cloud security depends on:
- Strong identity governance
- Least-privilege enforcement
- Continuous permission analysis
Ignoring identity risk undermines even the strongest cloud security architectures in the UAE.
3.3 Data security posture management becomes essential
Enterprises often don’t know:
- Where sensitive data resides
- Who can access it
- Whether it is encrypted properly
Modern cloud security strategies for UAE enterprises require continuous data discovery and classification, not annual audits.
3.4 Policy-as-Code becomes the standard
Manual approvals and static policies cannot scale in cloud environments.
By 2026, policies are:
- Automated
- Version-controlled
- Enforced consistently across environments
3.5 Encryption maturity increases
Encryption is no longer optional. UAE enterprises are expected to manage:
- Encryption at rest
- Encryption in transit
- Encryption key ownership and rotation
3.6 AI-assisted detection and response
Security teams use AI to:
- Detect anomalies faster
- Reduce alert fatigue
- Prioritize real threats
This is critical as environments grow more complex.
4. UAE-Specific Cloud Security & Data Protection Considerations
Cloud security in the UAE must align with data protection expectations, industry regulations, and audit readiness.
Key considerations include:
- Data residency awareness (knowing where data lives)
- Sector-specific sensitivity (finance, healthcare, government)
- Clear accountability under shared responsibility models
- Ability to produce evidence during audits
UAE enterprises that succeed focus on continuous compliance, not periodic remediation.
5. Reference Architecture: Securing Multi-Cloud Environments (2026 Model)
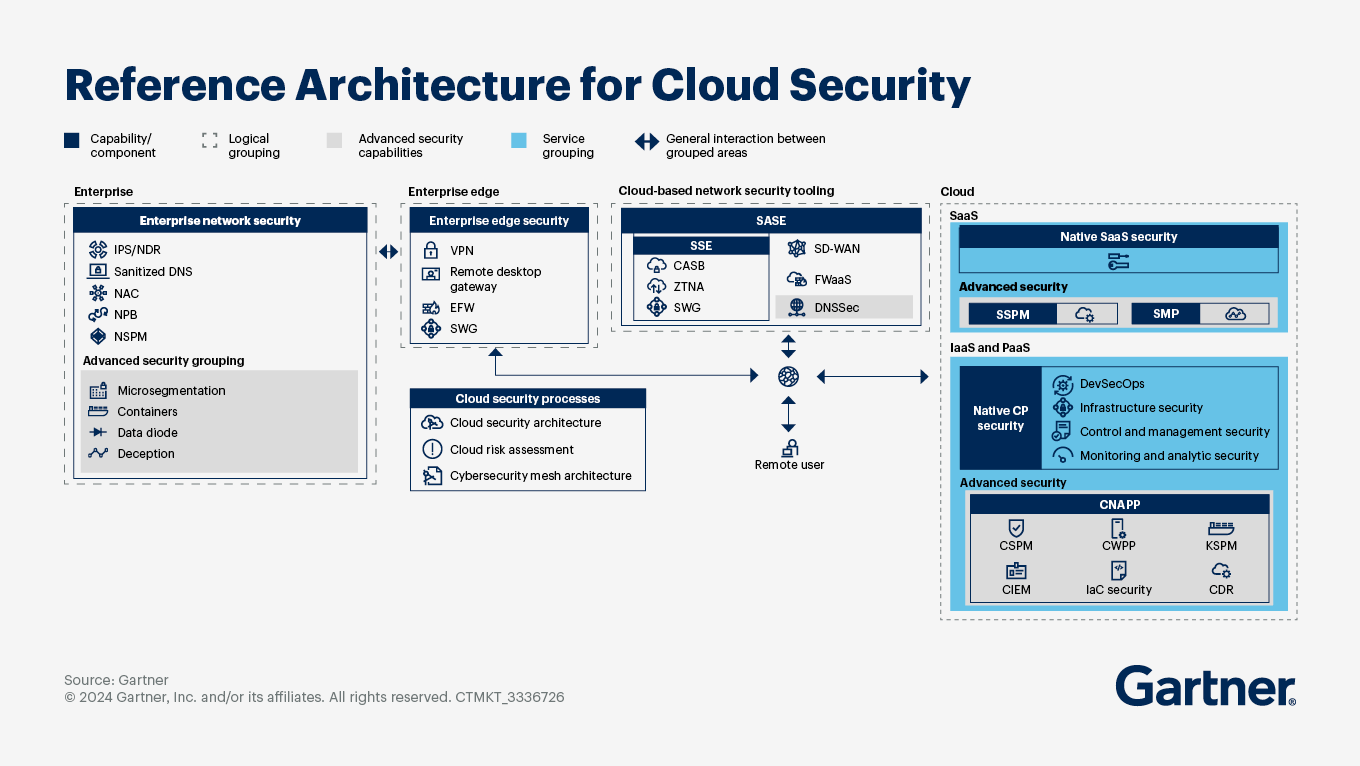
A strong cloud security posture is built on five interconnected planes:
5.1 Identity & Access Plane
- Centralized identity management
- Strong authentication
- Privileged access controls
- Continuous permission monitoring
5.2 Policy & Governance Plane
- Infrastructure as Code
- Automated policy enforcement
- Guardrails instead of manual approvals
5.3 Workload & Application Plane
- Secure configurations
- Vulnerability management
- Runtime threat detection
5.4 Data Protection Plane
- Data discovery and classification
- Encryption and key management
- Controlled access to sensitive information
5.5 Detection & Response Plane
- Centralized logging
- Security operations workflows
- Tested incident response plans
This architecture ensures consistency, regardless of how many clouds are in use.
6. Cloud Security Best Practices for UAE Enterprises
Effective cloud security best practices focus on outcomes, not tools:
- Reduce attack surface through configuration control
- Prevent identity abuse with least-privilege access
- Protect sensitive data continuously
- Detect threats early
- Respond consistently across environments
- Prove compliance at any time
When these outcomes are achieved, security becomes a business enabler rather than a blocker.
7. How to Secure Multi-Cloud Environments: A 90-Day Plan
This phased roadmap explains how to secure multi-cloud environments for UAE enterprises by focusing first on visibility, then control, and finally long-term resilience without disrupting ongoing business operations.
Days 0–30: Visibility & Baseline
- Inventory all cloud assets
- Centralize identity management
- Enable comprehensive logging
Days 31–60: Control & Prevention
- Enforce security posture policies
- Implement data classification
- Reduce excessive permissions
Days 61–90: Resilience & Response
- Test incident response workflows
- Validate backups and recovery
- Establish executive-level reporting metrics
By day 90, organizations should have measurable risk reduction and audit-ready visibility.
8. Industry Use Cases in the UAE
Financial Services
- High-sensitivity data
- Strong access controls
- Continuous monitoring
Healthcare
- Patient data protection
- Secure data sharing
- Audit-friendly controls
Government & Regulated Entities
- Strong governance
- Clear accountability
- Proven compliance evidence
Mid-Market Enterprises
- Scalable security
- Cost-effective protection
- Reduced operational overhead
9. Common Cloud Security Mistakes UAE Businesses Still Make
- Relying solely on default cloud security
- Ignoring identity risks
- Treating compliance as a yearly exercise
- Fragmenting security tools
- Failing to test incident response
These mistakes persist because cloud security is often implemented reactively instead of strategically.
10. Measuring Cloud Security Maturity in 2026
- Level 1: Reactive and manual
- Level 2: Tool-driven but fragmented
- Level 3: Policy-driven and consistent
- Level 4: Automated, auditable, and resilient
Most UAE enterprises aim to reach Level 3 or 4 to support growth without increasing risk.
FAQs
- What is cloud security in the UAE?
Cloud security in the UAE focuses on protecting data, identities, workloads, and compliance across cloud environments while aligning with regional regulations. - How is multi-cloud security different?
Multi-cloud security ensures consistent protection across multiple cloud platforms, avoiding gaps and misconfigurations. - Is cloud data safe for UAE enterprises?
Yes, when proper security architecture, access control, and data protection practices are implemented. - How long does it take to secure a multi-cloud environment?
A strong baseline can be achieved within 90 days, with ongoing improvements over time.
Final Thoughts: What UAE Leaders Should Do Next
Cloud Security UAE in 2026 is about architecture, automation, and accountability.
UAE enterprises that succeed:
- Design security holistically
- Focus on identity and data protection
- Embed security into operations
- Measure maturity continuously
Multi-cloud environments are here to stay. Securing them effectively is no longer optional it is a competitive advantage.


