File Integrity Monitoring
File integrity monitoring for Windows, Linux and network devices
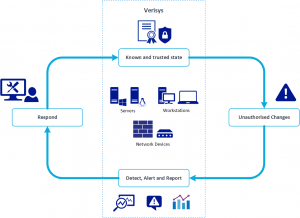
File integrity monitoring (FIM) detects and reports changes to critical files like system, application, and configuration files. Unmonitored systems may be at risk from unauthorized changes – resulting in operational downtime, security or confidentiality infringements, or compliance violations. By implementing the Verisys File Integrity Monitoring system you can be confident that your systems are in a known and trusted state.
The Verisys console and agents enable widespread monitoring and reporting of your business systems so that, in the event of discrepancy detection, you can act quickly to prevent, mitigate, or rectify the situation. Organizations implement FIM solutions for securing their systems from threats such as zero-day attacks and meeting compliance regulations such as PCI DSS, HIPAA, NESA, ADSIC, ADHICS, Malaffi, ISR, ISO 27001, FISMA, GDPR, and SWIFT.
File Integrity Monitoring with Verisys
Verisys File Integrity Monitoring gives you the ability to detect changes to system objects and network device configuration, ensuring your systems remain in a known and trusted state.
DETECT CHANGES:- Detect changes to Windows and Linux files, Windows registry objects, and network device configurations.
ALERT AND RESPOND:- Automated alerting means your key personnel will be rapidly alerted when discrepancies are discovered.
REPORTING:- Clear, concise reports at different detail levels in a variety of formats.
COMPLIANCE:- Detects and notifies of changes, meeting PCI DSS requirements, as well as applying to SOX, FISMA, HIPAA, ADSIC, ISR, Malaffi, NESA, SWIFT and more.
EASE OF USE:- Get started in minutes with our operating system and application templates for common system configurations.
AUTOMATION:- Automate integrity checks that notify, report, and respond when discrepancies are detected.
Respond Rapidly with Automated Alerts
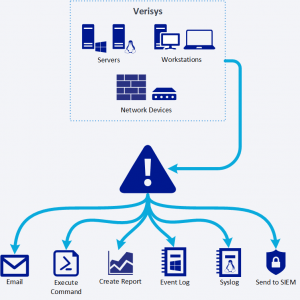
When suspicious activity is detected it is crucial that you are able to identify the key information and respond rapidly. With automated alerts, Verisys will provide clear, concise reports and notifications showing exactly what has changed.
When an integrity check detects data discrepancies it is crucial that you are able to identify the key information and respond rapidly. Automated alerting means that Verisys will provide clear, concise reports that will enable you to quickly ascertain which files or registry entries have been modified, and allow you to compile ‘data forensic’ evidence.
Using the Verisys central administration console you can set a priority threshold (low, medium, high, or emergency) for each automated integrity check so that you can take action depending on the level of discrepancy that has been detected. Based on your configuration Verisys will automatically send an email, write to the Windows event log, send events to Syslog, run an arbitrary command, or save a copy of the discrepancy report.
Centralized Management
Verisys central administration console allows you to configure and control all of the File Integrity Monitoring agents deployed across your enterprise. The central console simplifies the management of large or distributed agent deployments and enables centralized integrity checks, reporting, and licensing administration.
Rulesets to monitor servers, workstations, and network devices can be configured and published to any number of agents using the Verisys console, which reduces errors and rollout time, and simplifies the implementation of compliance procedures.
Low Cost of Ownership
Verisys breaks all of the familiar FIM stereotypes by being very easy to use, budget-friendly, and more useable through its features for eliminating false positives. There’s a reason that major organizations worldwide are relying on Verisys to keep their assets secure and compliant. It gives you the ability to detect changes to system objects and network device configuration, ensuring your systems remain in a known and trusted state making it a cost-effective Tripwire® alternative.
SIEM Integration
What’s more, alerts raised by a SIEM can be traced back to the file integrity monitoring tool, which can provide all of the forensic data (who, what, when, how) for the event, allowing for quick and simple root-cause analysis.