



The Virtual CISO service uses a strong and detailed process to collect and store compliance evidence in a way that auditors love. A strong audit trail with blockchain-like technology assures that the evidence provided cannot be tampered with, without breaking the chain of trust that auditors require. Once submitted into the chain, the evidence is locked in and secured.
This method of evidence chain sealing ensures that the documents provided represent proof you are truly in control of your business processes.
The necessary information for example can be extracted from ticketing systems, so you don’t have to. Everything needed is extracted, validated, and stored within the evidence chain without your input.
It is vital that event-based evidence stays current. Old data is not something auditors like to see. We typically request that documents be added to the evidence chain at least four times a year, matching the intervals required by the SOC2 Type 2 standard. When this is not possible, the vCISO services adjust accordingly.
By adding the data into the same evidence chain as technical reports, policies, and procedures, a full timeline can be provided to auditors during their audits. That way, a fully linked set of evidence is provided to the auditor, demonstrating you are in control of your business.

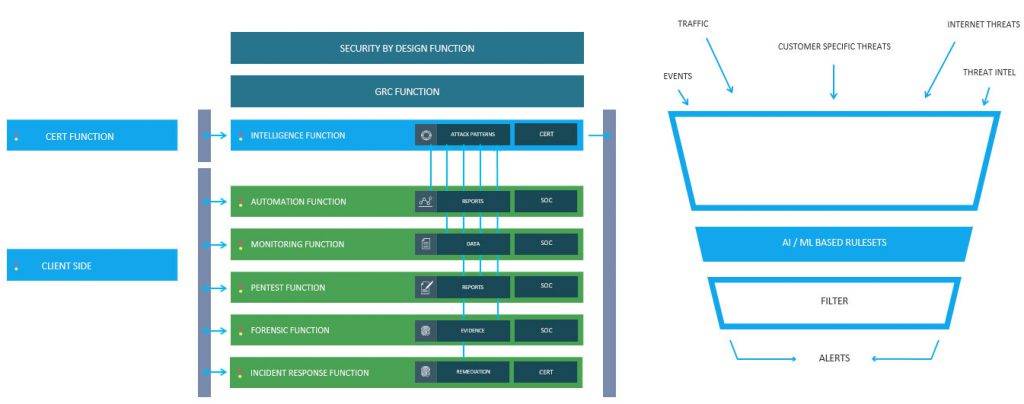
The team of Virtual CISO compliance specialists works around the clock on your behalf, working closely with the technical experts in the SOC. A lot of evidence can be gathered from these data sets.
Answers to policy-related topics in the compliance standards have to be retrieved from within the organization. It is important that we have access to, or receive the Information Security Management System (ISMS) information. Access to the policies and procedures provides the SOC team with much of the information and answers required.
Validation of control is governed and chased by the virtual CISO team so that these event-based reports can be added to the evidence chain. This can be things like reviewing user access controls, reviewing employee on and offboarding logs in correlation with these user access controls, firewall rule reviews, and even the change and incident management monitoring.
Based on the compliance guideline your company has to adhere to, different questions are asked and follow-up is actioned by the SOC team.
Proving to an auditor that you are demonstrably in control can be a painstaking and time-consuming process where information must be retrieved from dozens of systems. Furthermore, the integrity of this data must be proven to ensure it hasn’t been tampered with.
The vCISO service helps eliminate all of these concerns by providing trouble-free and secure evidence chains, with flawless timeline reporting and proven data integrity. vCISO combines technical data from our MDR services, with event-driven customer evidence from internal systems as well as policies and procedures from within the ISMS. This unique combination of data allows us to create a one-stop solution that is modular, flexible, and more importantly, affordable!
Copyright © 2026 Clouds Dubai, Powered by Oktohut