A Compromise Assessment is a high-level review of the security posture of an organization to identify if they are already compromised or breached. Compromise Assessment checks if any attacker activity or unauthorized access is already present in your network by analyzing data, logs, and existing telemetry, to identify indicators of compromise, advanced persistent threats, or threat actors present in the environment.




During a Compromise Assessment, we detect indicators of compromise and hidden malware within your IT infrastructure and assess the scale of damage to determine which assets in the network were attacked and how the attack happened.
During a Compromise Assessment, we detect indicators of compromise and hidden malware within your IT infrastructure and assess the scale of damage to determine which assets in the network were attacked and how the attack happened.

Frequently used tools: We will use tools such as Velociraptor, Security Onion, SIFT Workstation, KAPE, Registry Explorer, Volatility, Wireshark, Nessus, UAC (Unix-like Artifacts Collector), CyLR, and Custom PowerShell Scripts.
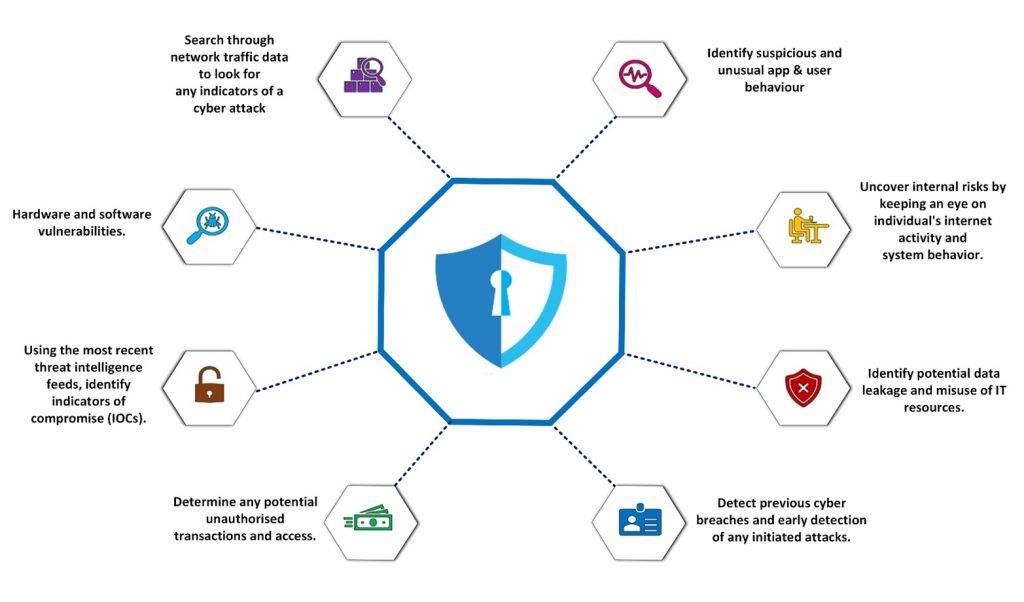
The purpose of the Compromise Assessment is to analyze a customer’s environment end to end and provide higher visibility into their existing security posture across a wide field of view against sophisticated attacks. This is a broad security assessment for those organizations that need a macro view of their environment to ensure all of the industry-recommended security best practices are implemented, vulnerabilities are fixed, and security controls are in alignment with the information security policy and compliance standards against various threat actors.
This makes sure that threat monitoring is effective to proactively hunt malware with the latest threat intelligence, policies and standards are well developed and maintained, and cyber defenses, access control & content filtering are effective. It also makes sure that the risk register is properly maintained, logging and auditing are proper, incident response measures are well developed and implemented, Patch Management is up to date, the security architecture is flawless and endpoint detection and network security controls are properly implemented to prevent any security breaches.
The data derived in the form of a detailed report from Compromise Assessment will lead to the presentation of the findings report outlining any key observations of general security risks, threats, vulnerabilities, and recommendations to remediate the identified issues for better cyber-security. These recommendations are a combination of industry-leading tools, industry best practices, and professional services suitable to the customer environment. Implementation of a solution or remediation of any identified issues will be available as a separate service if requested by the customer.
Copyright © 2026 Clouds Dubai, Powered by Oktohut