miniOrange provides Identity and Access Management (IAM) solutions by providing secure access to any cloud, web, and legacy app with strong authentication methods and single sign on to any enterprise application.
miniOrange 2 FACTOR AUTHENTICATION
2 Factor Authentication Products ensure the right set of eyes have access to your sensitive information sitting on the cloud or on-premise. Two-Factor Authentication (2FA) is the process of the authentication in which you have to provide two factors to gain access. First Factor is the one that you know username and password and the second factor is what you might have as unique like a phone (For OTP) or Fingerprint. This additional layer prevents unauthorized persons from accessing the resources even if they know your username and password.
Overview
miniOrange authentication service combines something you know or something you have with someone you are to reliably confirm your identity.
Using Two Factor Authentication
The most practical way to strengthen authentication is to require a second factor after the username/password stage. Since a password is something that a user knows, ensuring that the user also has something or using biometrics thwarts attackers that steal or gain access to passwords.
Traditional two-factor authentication solutions use hardware tokens (or “fobs”) that users carry on their keychains. These tokens generate one-time passwords for the second stage of the login process. However, hardware tokens can cost up to $40 each. It takes time and effort to distribute them, track who has which one, and replace them when they break. They’re easy to lose, hard to use, and users consistently report high levels of frustration with token-based systems.
Your choice of the second factor
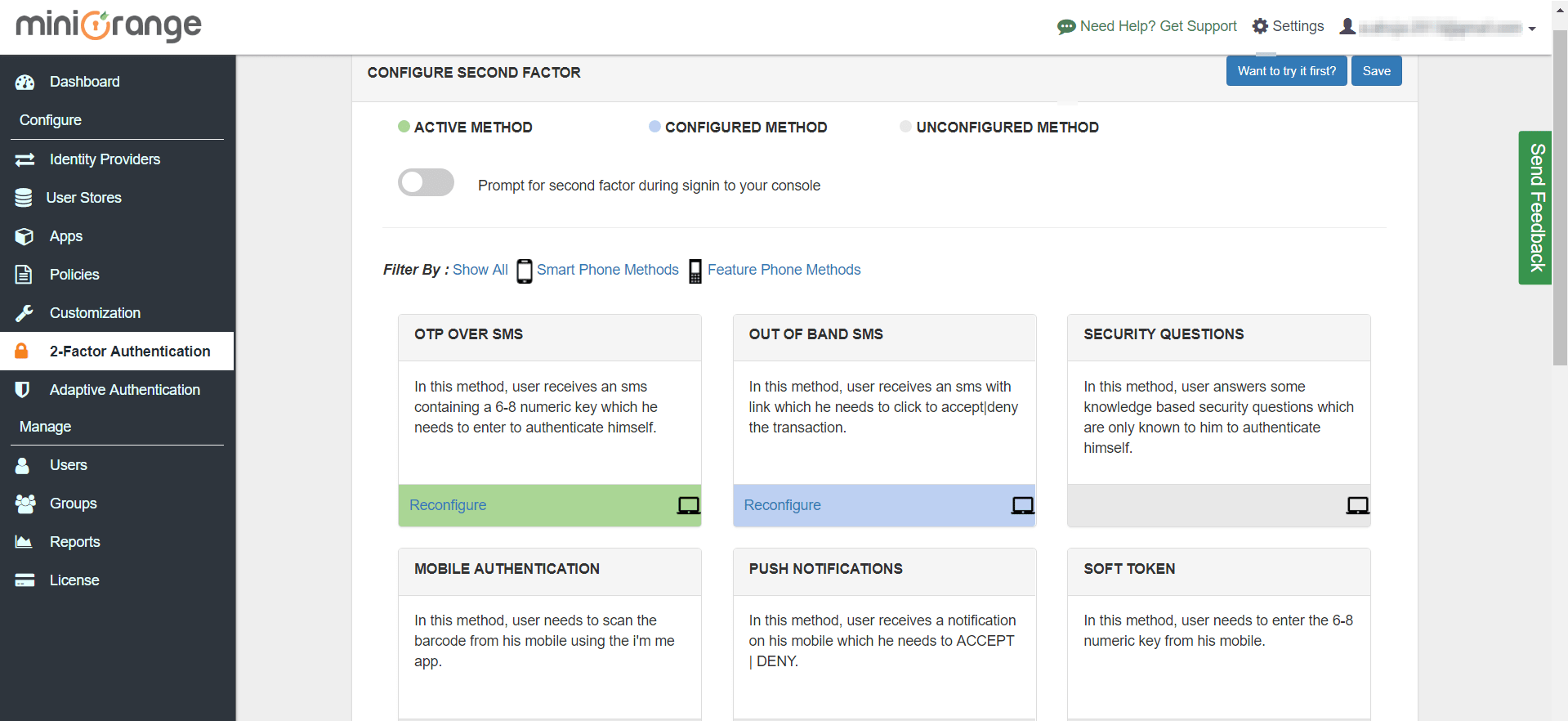
The authentication service has 15+ authentication methods.
One time passcodes (OTP) over SMS
OTP over Email
OTP over SMS and Email
Out of Band SMS
Out of Band Email
Soft Token
Push Notification
USB based Hardware token
Security Questions
Mobile Authentication
Voice Authentication (Biometrics)
Phone Verification
Device Identification
Location
Time of Access
User Behavior
You can choose from any of the above authentication methods to augment your password-based authentication. miniOrange authentication service works with all phone types, from landlines to smartphone platforms. In the simplest case, users just answer a phone call and press a button to authenticate. miniOrange authentication service works internationally and has customers authenticating from many countries around the world.
Key Features
Authentication service provides 15+ authentication methods and integrates with applications that do or do not support standards like SAML, OpenID, OAuth, WSFED, etc. It also integrates with enterprise products that support legacy protocols like RADIUS. It also integrates with application servers like Websphere, Weblogic, and Tomcat. In addition to that, it integrates with Spring. It also can be used to augment authentication for products like Siteminder. Our product is available as a service on the cloud or it can also be installed on-premise.
Overview
miniOrange SSO server allows you to log in to your applications without re-entering your credentials after you authenticate yourself into the Windows domain.
miniOrange achieves this by, installing a component on the Windows Server that, basically acts as an Identity Provider. When the user tries to access a cloud application like Salesforce, the request is sent to the miniOrange SSO Server which in turn asks the miniOrange SAML module installed in the Windows machine if the user can be logged in, and performs SSO based on the response from the module.
This involves 3 steps basically:
- Enable Windows Authentication and configure SSO applications of interest in the Windows Machine.
- Installing the miniOrange SAML module in Windows and configuring it with the miniOrange SSO server.
- Add the miniOrange SAML module ( installed on the Windows Machine )as an Identity Source in the miniOrange SSO server.
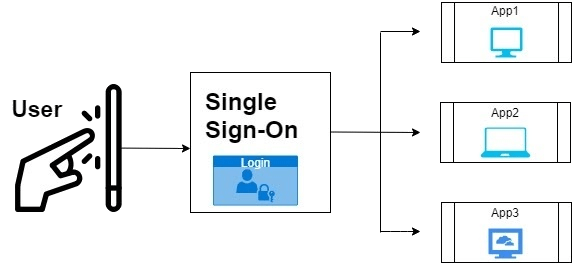
How SSO works?
- The user requests access to their desired application/website. That application/website is from the Service Provider.
- The Service Provider redirects the SSO Request to Identity Provider for authentication.
- The Identity Provider sends back the SSO Response to the Service Provider.
- On receipt of the SSO Response, the user is granted access to log in and access the resource or application.
- Now the user can access all the other applications/websites from the Service Provider which are configured for SSO.
Benefits of SSO
Boost Productivity:- Saves time by accessing all resources with just one click. Easily integrate with your application which supports SAML, OAuth 2.0, etc.
Flexible IdP:- Enable Single Sign-On for users without having to move users from their existing user store. A variety of user stores like Identity Provider, OAuth Provider, Active Directory, Database, etc. are supported.
Branding / Customization:- We provide customization on our products which are platform-independent and they can be easily accessed by an end-user.
Pay as you Go:- Pay As You Go subscription model with affordable fees and 24/7 support.