Having your Microsoft 365 and Active Directory in the cloud has many benefits, but attackers can also abuse this ease of access. User credentials are being leaked and stolen every day, with attackers abusing these stolen credentials and trying to log into your organization remotely. Bluedog’s Microsoft 365 Security Monitoring can protect your staff and information wherever they are; we can protect your company’s extended network.
Bluedog helps you to secure your Microsoft 365 environment. It can take in all Microsoft 365 events, as well as the Azure Security Center with a few clicks. Employees are not always in the office but are working elsewhere. There might be suspicious account login attempts from outside the office, data exfiltration from SharePoint, or phishing emails that arrive in your employee’s email.
Bluedog Microsoft 365 Security monitoring is a managed service that detects if email accounts are hacked into and abused by attackers. This is a common attack that is next to impossible to prevent with automated solutions. Bluedog Microsoft 365 Security Monitoring can detect and take actions if accounts are breached and abused by a malicious third party. It identifies emails sent to victims on behalf of the breached user to identify email rules that the attackers create during the MITM attack to intercept the replies. The solutions help in spotting these attacks very fast and alerting the compromised users so that immediate actions are taken.
If you’re one of the millions of businesses using Microsoft® 365 you need to think seriously about security monitoring for your Microsoft® 365 tenancy.
Your staff working remotely or from home are vulnerable. You can’t monitor their network when they are working away from the office.
It’s relatively easy for cybercriminals to gain access to your Microsoft® 365 tenancy in the same way that they can gain access to your office network.
Because Microsoft® 365 is cloud-based, it’s more difficult for you to even know there’s been a breach!
You need a way of ensuring the safety of your information even for employees working from home or remotely.
If you are using Microsoft 365 within your organization and are looking to secure your environment, then look no further for Microsoft 365 Security Monitoring.
Employees working from home:- It is very difficult to monitor devices which aren’t on the company premises. With our Microsoft 365 and Azure Active Directory monitoring, these devices are also included. No more devices outside the network are missed out.
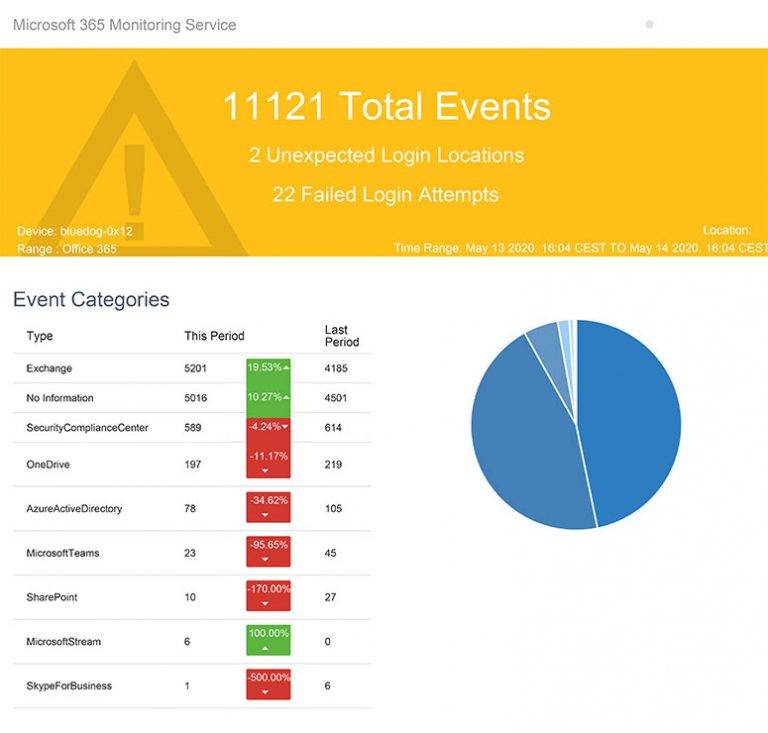
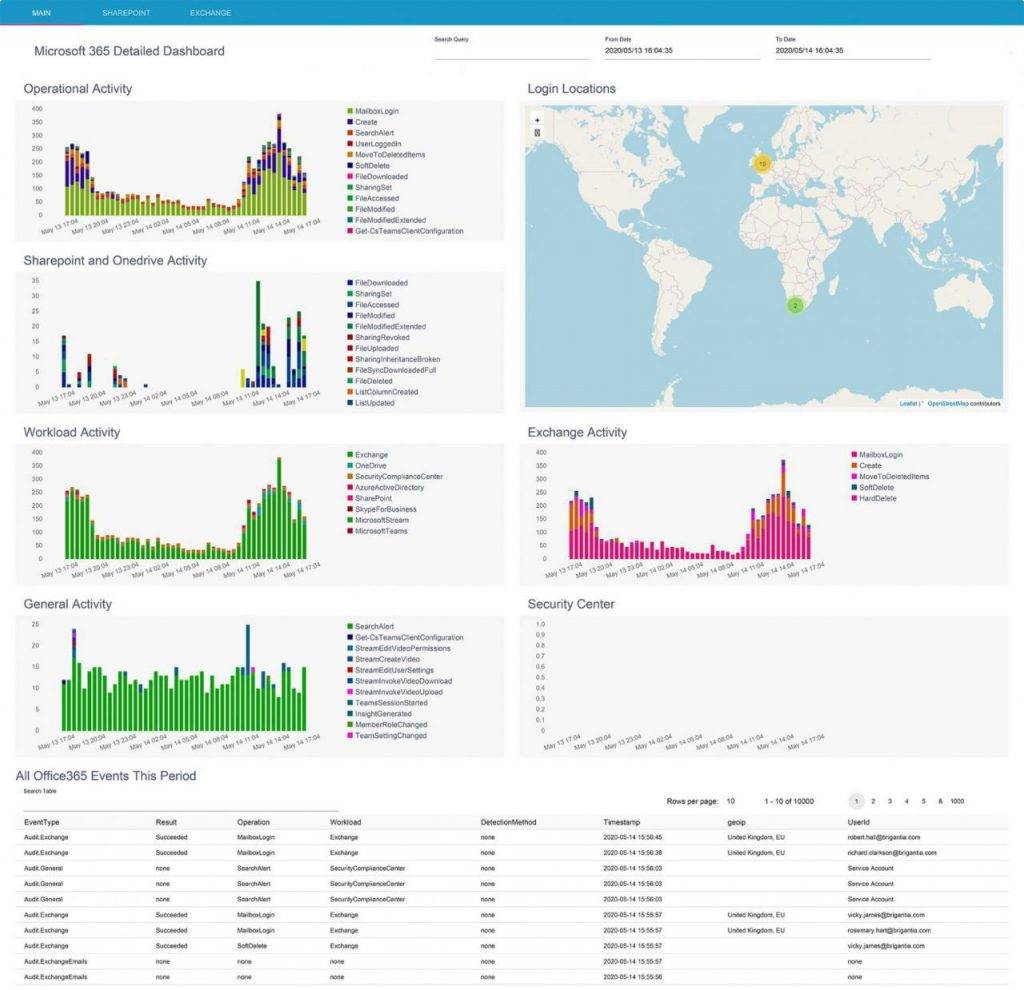
There are always employees on the road with a company laptop that isn’t being monitored traditionally. With our Microsoft 365 and Azure Active Directory monitoring, these devices are now fully monitored.
The Microsoft 365 monitoring service can detect risks ranging from suspicious account logins and data downloads to phishing emails arriving in an employee’s inbox. The service, which is the only one of its type that is overseen by a live cybersecurity team, costs from just $2.5 per user per month and can be switched on remotely. The Bluedog office 365 security monitoring service integrates with the Azure Active Directory and matches the company’s internal network data with its Microsoft 365 usage to identify abnormal behavior. Any suspicious incidents will automatically alert the team at its security operations center who can then investigate and act upon them.
Bluedog will detect breaches of cloud-based systems that would not trigger conventional defenses such as anti-virus solutions and firewalls. The service highlights unusual login locations or lateral movement so the team will be able to spot the attacker navigating across the network. Having a human on hand to check and interpret data can make all the difference. Bluedog Microsoft 365 monitoring service is the only one of its type that is backed by an expert team that has full sight of all alerts and can make an informed decision.
The service also allows companies to see which files and emails have been accessed, downloaded, deleted and from which account and location so they can check if data has been stolen. To ensure companies’ privacy, Bluedog is only able to see the filenames and locations, and not the contents of files. According to the Cyber Security Breaches Survey 2020, which was carried out before the global lockdown, corporate staff in 53% of the businesses were regularly using their own laptops or devices.
Copyright © 2026 Clouds Dubai, Powered by Oktohut