Labyrinth Webinar on 24th April 2025
Get the most efficient tool to detect and stop malicious activities inside your corporate network
Labyrinth webinar on Deception-based Intrusion detection
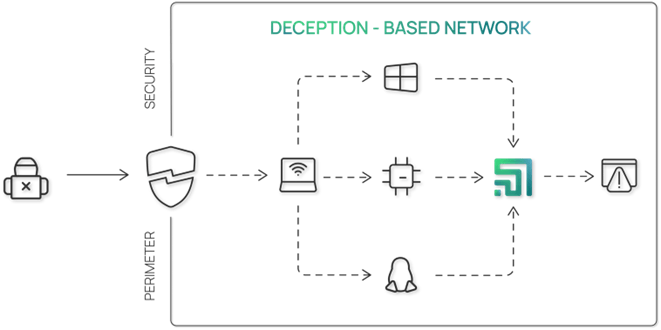
In today’s rapidly evolving threat landscape, traditional cybersecurity tools like firewalls and Unified Threat Management (UTM) systems are no longer sufficient. While these solutions focus on prevention, the need for advanced tools to detect and respond to threats has become critical. One of the most innovative approaches in this area is deception technology, which not only monitors networks but also misleads attackers, protecting critical assets in the process. Labyrinth is a deception-based threat detection technology that identifies and blocks cyber-attacks from within a corporate network using honeypots and deception artifacts.
Key features:
Early Threat Detection: Detects suspicious activities at the initial attack stages using network decoys.
Accurate Alerts: Provides high-reliability alerts with less than 1% false positives.
Rapid Incident Response: Enriched security data aids in quick threat investigation and mitigation.
Proactive Defense: Engages attackers in controlled environments to analyze their techniques.
Targeted Attack Uncovering: Identifies attacker tactics, techniques, and procedures.
Post-Infection Detection: Identifies threats that bypass traditional security solutions.
Lateral Movement Recognition: Detects unauthorized internal network movements.
Dwell Time Reduction: Shortens the period attackers remain undetected within networks.
What Is Deception Technology?
Deception technology revolves around creating fake elements within an IT infrastructure—such as servers, applications, or data—that mimic real assets. These “decoys” are designed to lure attackers away from genuine resources while simultaneously alerting IT security teams to malicious activity. Every interaction with these decoys generates an immediate alert, enabling rapid detection and response.
A standout solution in this domain is the Labyrinth Deception Platform, which offers unique features like the Universal Web Point. This technology allows organizations to emulate any internal web portal used by employees. Imagine a scenario where an attacker encounters 20 fake web servers that look identical to production systems—watching their confusion can be both satisfying and highly effective in safeguarding real assets.
The Seeker – Adding a New Dimension to Security
The Labyrinth Deception Platform also includes a powerful feature called Seeker, which validates the effectiveness of existing security measures and policies. Seeker offers:
Validation of Security Controls: By simulating malicious behavior, Seeker tests tools like EDRs (Endpoint Detection and Response) and NGFWs (Next-Generation Firewalls) to ensure they function as intended.
Policy Validation: The Seeker identifies misconfigurations or violations of security policies, ensuring compliance and reducing the risk of breaches caused by human error.
Security Team Efficiency Evaluation: The tool assesses how quickly and effectively SOC analysts or Security teams respond to simulated threats, helping organizations optimize their incident response processes.
Register for the Labyrinth webinar now
Register now for the Labyrinth webinar scheduled for 24th April 2025 at 3.00 PM UAE time.
Register for the Labyrinth webinar at the earliest as seats are limited !!!