Monero, Coinhive, cryptojacking, website script injections to mine cryptocurrency. What’s all the fuss?
It’s time someone posted a simple, easy to follow explanation of why everyone is talking about this and why you should also upgrade your security.
The short story: online thieves can now steal your money and your information, while also driving up your power bill and possibly killing your computer hardware.
What is blockchain?
Blockchain was invented by Satoshi Nakamoto back in 2008 and is the base principle of Bitcoin and most other cryptocurrencies. Not only he invented Bitcoin, but, with blockchain, he solved a very big challenge when it comes to anyone spending money online or receiving money:
A digital file can be copied, modified or downright faked. While you can’t exactly Xerox a $10 bill and give it to your friend, a digital bill could be copied, so that two people could spend that exact bill. There was also another problem with digital currency: in order to verify that the bill was the original and not a copy or a fake, you needed someone to actually do the verifying. Usually, the bank or a third party like Paypal handles this process, acting as an intermediary between a buyer and a seller.
But what happens when you don’t trust the bank with your money? Or what if Paypal raises its fees so much that you feel robbed? Or what if the bank is hacked?
By putting so much power into the hands of a third party, users get exposed to a lot of risks. Enter blockchain and the reason why you’re hearing about it everywhere. It’s the promise it holds. The blockchain protocol eliminates the middleman by making everyone an active participant in the transaction.
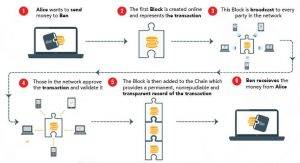
It’s easier if you think about it like torrenting software. In the past, you’d download a file from a single user or server, which was slow and obnoxious. Using torrents, you download hundreds of tiny pieces from hundreds of your peers who have the files on their computer. With blockchain, every time someone makes a transaction, that transaction is recorded in a block so that it remains permanently available.
When the next block is created, it will contain a cryptographic record of the previous block, essentially holding that previous’ block transaction history. As more and more people send money, more and more blocks are created and linked to one another into the blockchain. If someone wanted to hack a transaction or duplicate it, they’d have to attack the entire blockchain.
Who links these blocks?
In the case of “classic” money, it’s someone like a bank or Paypal. With cryptocurrency, everyone using the coin contributes. Well, not quite everyone. The people or machines that link these transactions are called miners. In exchange for a small fee, they link together the transactions and create the blocks to be added to the blockchain.
They accomplish this by solving complex mathematical equations using their computer’s processor or graphics card. In some cases, there are special computers designed specifically for mining cryptocurrency, called ASICs. Here is a blockchain diagram to better explain the concept.
Currently, the blockchain is mostly used for financial transactions. It’s mainly a platform for digital money, though it can be used in a myriad of ways. When there’s a need to replace a middleman for record-keeping, blockchain is a possible solution because it turns the process into a sort of democracy. That’s why decentralization is such a popular term nowadays.
What is Monero?
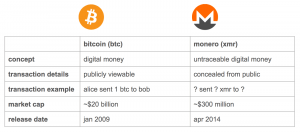
Monero (shortened to XMR) is an anonymous, encrypted, almost untraceable cryptocurrency. It’s virtual money like Bitcoin (BTC), but it’s also a coin whose route is almost impossible to follow. Of course, as you can see, a lot of these people do not necessarily have the best intentions. Because of the intense media coverage, you probably know a lot about Bitcoin. If you don’t, we went in-depth on its history and how to be safe from hacks when investing.
What is the difference between Bitcoin and Monero?
The latter coin’s official website explains the most important reason why Monero is a cyber criminal favorite. With Bitcoin, any BTC can be tracked by anyone back to its creation coinbase transaction. Therefore, if a coin has been used for an illegal purpose in the past, this history will be contained in the blockchain in perpetuity. Currently, some large Bitcoin companies are blocking, suspending, or closing accounts that have received Bitcoin used in online gambling or other purposes deemed unsavory by said companies.
So what does Monero do differently?
Monero offers confidential, untraceable transactions.
Oh, by the way, the coin’s market cap is now more than 4 billion USD according to the latest charts. Due to its design fundamentals and a strong emphasis on privacy, Monero is a Holy Grail to a lot of people:
* Libertarians, anarchists, cypherpunks and other anti-establishment groups
* Internet activists who want to get funding from their supporters without revealing too much information
* Citizens who, for one or another reason, do not want their government to know how many assets they own
* People who lost trust in the banks and look for a new way
* Members from groups like the infamous Anonymous who target users and organizations in the name of a cause or for just good old trolling
* People who make a living online (content creators like bloggers or YouTubers, marketers etc)
* Serious cyber criminals that go for big targets like the NHS, other government sites, Tesla’s cloud servers and so on.
Let’s grab on to this last group. It’s the one that forces you to increase your online security measures, after all.
How blockchain can enable the cybercriminal industry
Want to know why cryptojacking is such a big threat to your financial security? Want to know why cyber security experts are scrambling to counter so many attacks?
Beyond complicated concepts and fuzzy acronyms, it’s quite simple. In the past, cyber criminals tried to steal your credit card info so they could use your money. Now, cyber criminals can steal your computer’s resources to create money,
In the near future, they will do both. Why not create malware that uses your computer to create money and also tries to steal your actual money?
With Bitcoin, stealing is possible. It’s, however, riskier for malicious hackers and not that profitable. The Bitcoin mining process is now too resource intensive for regular setups and is done on specialized hardware.
With Monero, stealing is extremely easy. Why?
Because it can be done on consumer grade CPUs. Monero is also anonymous and untraceable. Even if the authorities were inclined to help you in case of an attack (though they’re still struggling with the general cryptocurrency concept) Monero makes it almost impossible for them to identify the perpetrators.
The creators of WannaCry, one of the worst ransomware attacks in history, converted their Bitcoin gains to Monero so that the authorities could not follow the “money”. This is a simple explanation of why #Monero is a favorite among online criminals
Moreso, there is an online, free to use tool that makes it easy for thieves to obtain Monero. It’s called Coinhive.
What is Coinhive?
Coinhive is simply a Monero miner that uses Javascript, the most popular programming language. This code can be embedded on any web page. Once you access that page, it uses your computer processor (CPU) to mine Monero. In a perfect world, the Coinhive script would be used by content creators on their pages. You’d visit their site without being badgered by ads.
You’d read an article or watch a video. While you were doing that, the creators of that content would be paid simply by using a few of your computer’s resources. This is exactly what the famous Salon.com did – they implemented Monero to obtain revenue and give their visitors a chance to avoid ads.
However, it’s not a perfect world.
What cryptojacking is and how it affects you
Malicious hackers can target the websites you visit and implement the Coinhive script. It has happened to thousands of websites, from pizza shops to blogs and worse, health organizations and government pages. The Coinhive script has also been introduced in ads, the Internet Explorer browser, dozens of Android apps and more. Those running the websites or ads had no idea that there was an unwanted script, one that was using the viewer’s computer to mine Monero.
Such an attack is called cryptojacking, short for “cryptocurrency hijacking”. It’s stealing computer processing power to create cryptocurrency and make a quick, untraceable profit. Basically, without your consent, it turns your PC or device into a Monero miner. It’s also compromising hundreds of thousands of websites and targeting a lot of vulnerabilities.
Because malware often goes unnoticed by users and antivirus can’t really catch it, it’s a huge challenge to tackle. The Coinhive script can use 100% of the visitor’s CPU power and thus lower the lifespan of the hardware itself. When you view a Coinhive infected site or use an app, it’s like a thief breaks in your garage every night and takes your car to run errands. The car is still in the garage in the morning, but your mileage increased and there’s wear and tear on the machine.
Who knows where your car has been or what’s it been used for?
Moreover, with Monero malware packages, a malicious hacker can also put a surveillance camera in your car. Now, the hacker has free use of your car and, if you leave valuables in it, he can also steal those. It’s also a horrible attack for the website owners as well, calling into question their security measures and having users ask angrily “Why don’t you secure your business?”
What the future holds for cryptojacking and you
Unfortunately, Coinhive injections are attacks that will paint the 2018 landscape. Even if all businesses, websites and software apps manage to block it, the idea and technology are out there. There are hundreds, if not thousands of Coinhive copycats currently available or in the pipeline. There is no question that we will see more cryptojacking and other cyber threats, even if Coinhive and Monero become irrelevant.
Blockchain and cryptocurrency are revolutionary concepts and here to stay.
Even though what’s currently happening could very well be a bubble of hideous proportions, they are the face of the Web 3.0 and the immediate future of the Internet. However, as with all transitions and as with all financial issues, there are security gaps that you need to close. Here are the a few steps for you to achieve Internet security as a user.
What online security measures you need to avoid cryptojacking
1) Always protect your computer with an antivirus .
2) Antivirus is not enough! Modern malware sneaks past it. You also need an anti-malware solution to catch the threats before they reach your PC.
3) On any browser, both on desktop and mobile, use an adblocker. Only disable it if you trust a website completely.
4) Always update your software, because most cryptojacking takes place due to unpatched vulnerabilities.
5) Always use strong passwords or a secure password manager so that, in the event of an attack, your personal info is not compromised.
6) Knowledge of online security basics will always be useful, so consider signing up for a free course
For more information visit https://heimdalsecurity.com/blog/cryptojacking-monero-malware/