Penetration Testing Services are part of Security Assessment and Vulnerability Management for information security compliances like ISO 27001, PCI DSS, HIPAA, ADSIC, SIA (NESA) & ADHICS. Penetration Testing Services or VAPT are conducted for networks (Servers, Firewalls, Switches, Routers & Workstations) and Applications (Web & Mobile). It involves a simulated hacker attack on the infrastructure or applications to identify the vulnerabilities.
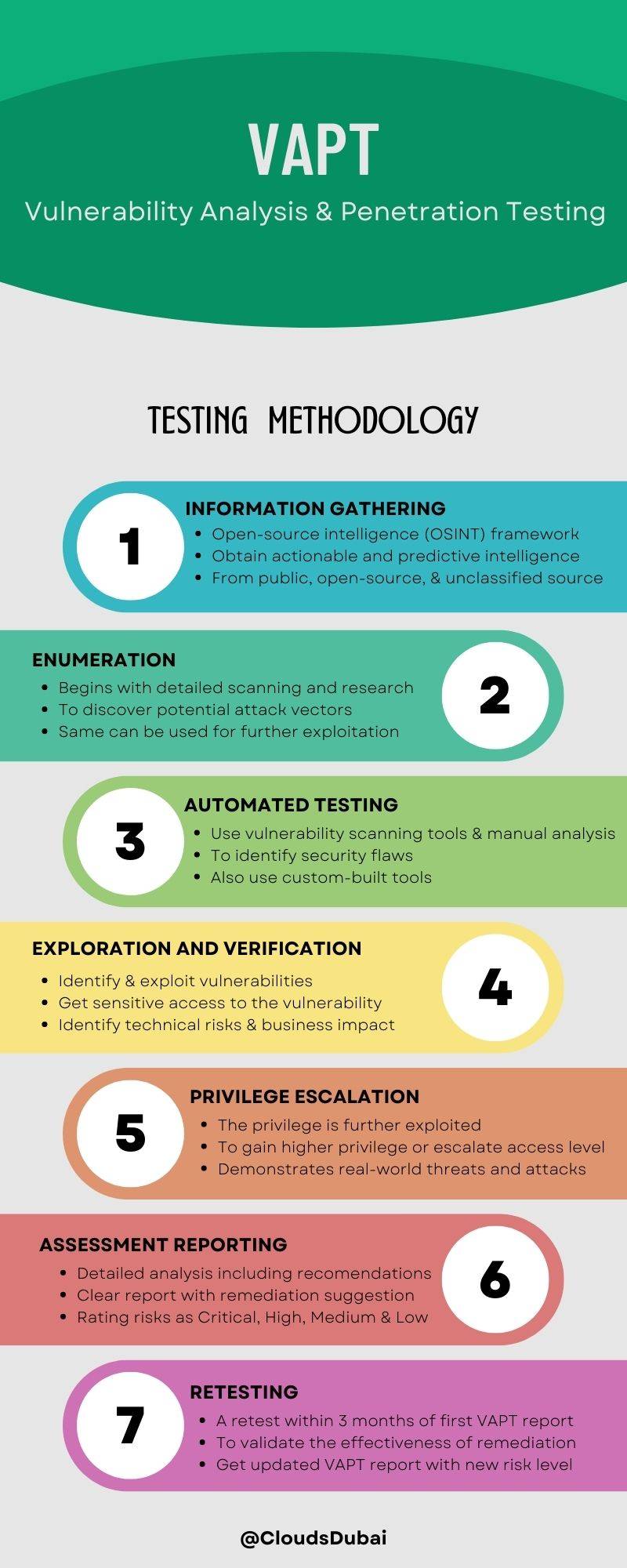
Penetration Testing Services involve various steps including Information gathering and enumeration. vulnerability analysis using automated scanners, exploitation of vulnerabilities, etc. A detailed VAPT report will be presented at the end of the activity. Identified vulnerabilities are risk rated as Critical, Hig, Medium, or Low. Each vulnerability will be provided with a detailed description of the vulnerability along with proof of exploitation and mitigation recommendations to fix the same. A retest will also be done as part of the VAPT exercise.
Penetration Testing Services for Compliance
VAPT testing is recommended as part of risk assessment for information security compliances like ISO 27001, PCI DSS, HIPAA, ADSIC, NESA, ADHICS, etc. We provide state-of-the-art Penetration Testing Services in the following scenarios:-
> Web Application/API Security
> Website Pen Testing
> Mobile Application Security (iOS & Android)
> Network Penetration Testing (Internal & External)
> Security Code Reviews
> Vulnerability Assessments
> Continuous Validations and Reports on Compliance
> Spear Phishing Campaigns
> Red Teaming
> Configuration Revies (Network/Cloud)
> Architecture Reviews
> Wireless Security Penetration Testing
> Compromise Assessment
> Incident Response
> Cyber Threat Hunting
The team members carrying out the Penetration Test would be qualified in one or more of the certifications given below:-
• Certified Ethical Hacker (CEH v6)
• Offensive Security Certified Professional (OSCP)
The purpose of Penetration Testing Services is to investigate the security of the environment, identifying vulnerabilities that could result in the compromise of the availability, confidentiality, or integrity of data. These vulnerabilities can then be remediated, lowering the risk of such compromises. Our process includes a consultative approach to working with clients to ensure that you gain the most from our testing. The following actions will be undertaken as part of the testing:
> A combination of automated and manual techniques will be used to form a list of potential vulnerabilities in the environment.
> We will then exploit the identified vulnerabilities if it is possible to do so without causing availability issues. Exploitation will be used to validate whether the vulnerability exists, determine what effects the vulnerability could have, and allow deeper inspection of the infrastructure.
> At the conclusion of testing, we will analyze the root cause of each vulnerability, consider the risks the vulnerability could present to the organization, and provide recommendations that will fix the vulnerability.
> A report will be issued containing the details of testing including the testing methodology, findings, technical and high-level recommendations, and risk analysis.
> Once the report has been delivered, we will also provide a follow-up meeting to debrief the client’s IT staff, and to assist in planning the remediation efforts.
Penetration Testing: How to Secure Your Network & Applications
As the world of technology becomes increasingly interconnected, the need for reliable network security grows. One of the best ways to ensure that your network & applications are secure is to conduct a penetration test, also known as a “pentest.” Penetration testing service is a type of security testing that simulates an attack on a computer system in order to find vulnerabilities that could be exploited by malicious actors. By identifying and addressing these vulnerabilities, you can significantly reduce the risk of your network & applications being compromised.
The Benefits of Penetration Testing services
Penetration testing services can provide a number of benefits for your organization. First and foremost, it can help you to identify vulnerabilities in your system & applications before they can be exploited by attackers. This allows you to take steps to fix the vulnerabilities before they can be used to harm your application & network. Additionally, penetration testing services can help you to assess the effectiveness of your current security measures. By seeing how well your system withstands an attack, you can make changes to improve its overall security. Finally, penetration testing services can help to educate your employees about security risks. By seeing how an attack unfolds, they can be better prepared to identify and defend against future attacks.
Penetration testing services can be an invaluable tool for keeping your network & applications safe and secure. By taking the time to test your system & application for vulnerabilities, you can help to ensure that it is as strong as possible against future attacks.
The Risks of Not Conducting Penetration Testing
Not conducting a penetration test can leave your network & applications vulnerable to attacks. If you are not regularly testing your system for vulnerabilities, it is likely that attackers will be able to find and exploit them before you are aware of the problem. This can lead to data loss, financial damage, and a loss of customer trust. Additionally, not conducting penetration tests can also lead to regulatory penalties. In some industries, such as healthcare, failure to conduct regular penetration tests can result in hefty fines.
Consequently, it is important to make penetration testing a regular part of your organization’s security strategy. By regularly testing your system for vulnerabilities, you can stay ahead of attackers and help to ensure the safety of your data and your customers.
The Cost of Penetration Testing Service
The cost of penetration testing service can vary depending on the size and complexity of your network. However, the average cost of a basic pentest is between $1,000 and $5,000. For a more comprehensive test, the cost can rise to $10,000 or more. While the cost of penetration testing service may seem high, it is important to remember that the cost of a successful attack can be much higher. By investing in penetration testing services, you can help to ensure that your network is secure and reduce the risk of costly attacks.
It is important to note that penetration testing is not a one-time investment. In order to keep your network secure, you should plan on conducting penetration tests on a regular basis. The frequency of your tests will depend on the size and complexity of your network, as well as the level of security you require. However, most experts recommend conducting penetration tests at least once per year.
How to Conduct a Penetration Test
If you are interested in conducting a penetration test, there are a few things you should keep in mind. First, you will need to choose a pentesting firm that is reputable and has experience conducting tests on similar networks. Second, you will need to decide what type of test you would like to conduct. There are three main types of tests: black box, white box, and gray box. Black box tests are the most comprehensive, but also the most expensive. White box tests are less expensive but still provide a good amount of information. Gray box tests fall somewhere in between. Once you have chosen a firm and a type of test, you will need to provide them with access to your network & application so that they can conduct the test.
The Tools of Penetration Testing Services
Penetration testers use a variety of tools to conduct their tests. These tools can be divided into two main categories: active and passive. Active tools are used to directly attack a system in order to find vulnerabilities. Passive tools are used to gather information about a system without directly attacking it. Some of the most common active tools used in penetration testing include hacking tools, exploit frameworks, and password crackers. Some of the most common passive tools used include port scanners, network mappers, and vulnerability scanners.
Active tools are generally more intrusive and can cause more damage to a system if used improperly. That’s why it’s important for penetration testers to have a good understanding of how these tools work and how to use them safely. Passive tools are generally less intrusive and can be used to gather a lot of information about a system without causing any damage.
The Results of a Penetration Test
After a penetration test has been conducted, the pentesting firm will provide you with a report detailing its findings. This report will include information on any vulnerabilities that were found, as well as recommendations on how to fix them. It is important to note that not all vulnerabilities can be fixed. In some cases, the only way to protect against an attack is to implement security measures that will detect and block it. However, by taking steps to fix the vulnerabilities that can be fixed, you can significantly reduce the risk of your network being attacked.
How to Secure Your Network Against Attacks
There are a number of steps you can take to secure your network against attacks. First, you should ensure that all of your devices are up-to-date with the latest security patches. Second, you should implement a firewall and configure it to block all incoming traffic from untrusted sources. Third, you should use strong passwords and enable two-factor authentication for all users. Finally, you should regularly conduct penetration tests to identify and address any vulnerabilities in your system.
By following the steps above, you can help to ensure that your network is secure against attacks. However, it is important to remember that no system is 100% secure. There is always a risk of being attacked, no matter how well-protected you are. Therefore, it is important to have a plan in place for how to respond if an attack does occur.