Secure Access for Active Directory Identities, Anywhere with UserLock
With MFA, SSO, and session management, UserLock can protect all employee access to corporate networks and cloud applications, whether on-site or remote.
UserLock provides a cost-effective, easy-to-use, and scalable access management solution for on-premises & hybrid AD environments to protect employee access to the corporate network & cloud applications, no matter where they work.
UserLock helps administrators manage and secure every user’s access, without obstructing employees or frustrating IT. To protect against external attacks and internal security breaches, organizations need to extend how they secure authenticated users’ access to company-sensitive files. UserLock’s access restrictions and real-time monitoring reduce the risk of security breaches and realize time and cost savings regarding tracking, auditing, and reacting to suspicious access events.
> MFA for Remote working
> Offline MFA
> Single Sign-On
> Contextual Access Controls
> Sessions Management
UserLock enables you to:
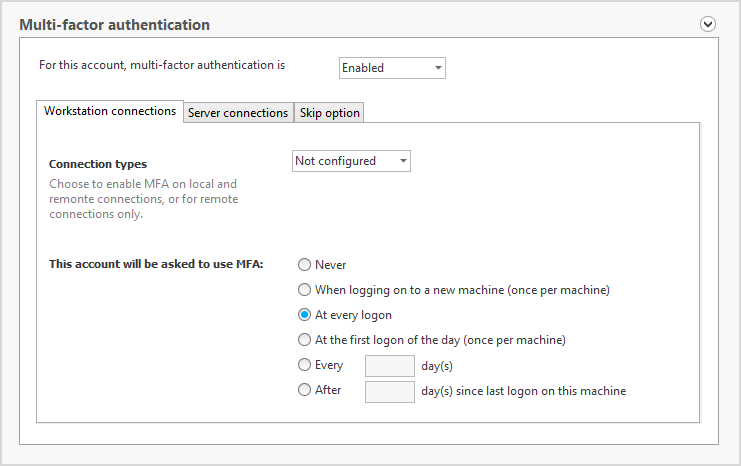
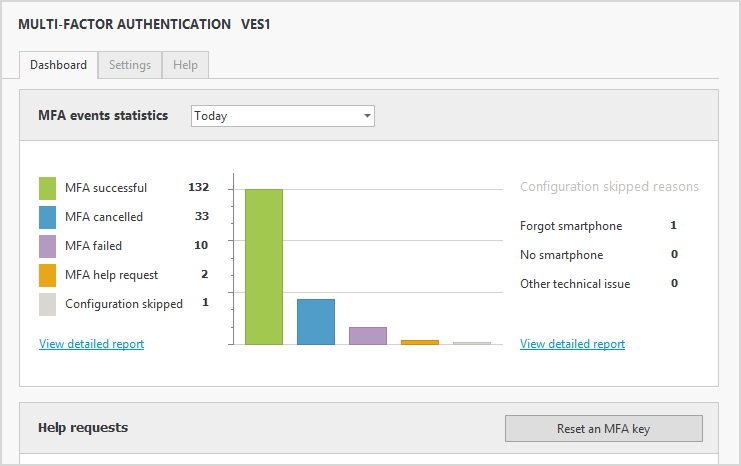
2 FACTOR AUTHENTICATION:-Enable customized, two-factor authentication (2FA) on Windows logon, Remote Desktop (RDP & RD Gateway), IIS, VPN, and Cloud Applications.
Single Sign-On:- Secure and frictionless access to Microsoft 365 and Cloud applications using only your AD credentials, from anywhere.
Contextual Access Management:- Set rules to authorize, deny or limit any login (including remote access), based on contextual factors:
- Origin: Computer (Windows & Mac), device & location restrictions (country, IP address, department, OU)
- Time: Logon hour restrictions, maximum session length & session time quota
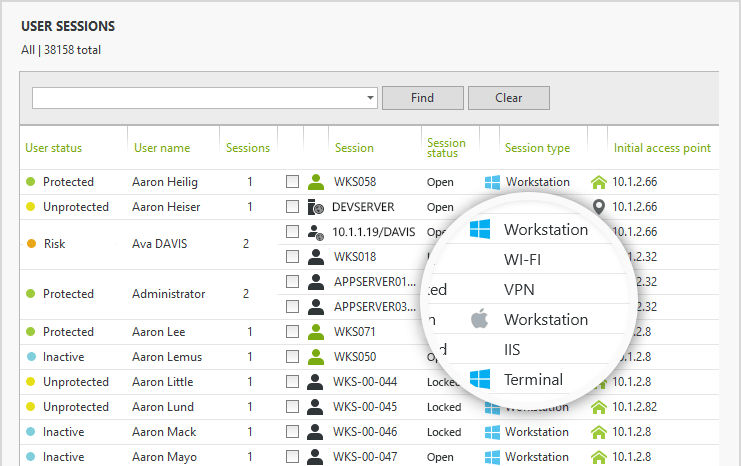
- Session type: Workstation, terminal, Wi-Fi, VPN, and IIS sessions
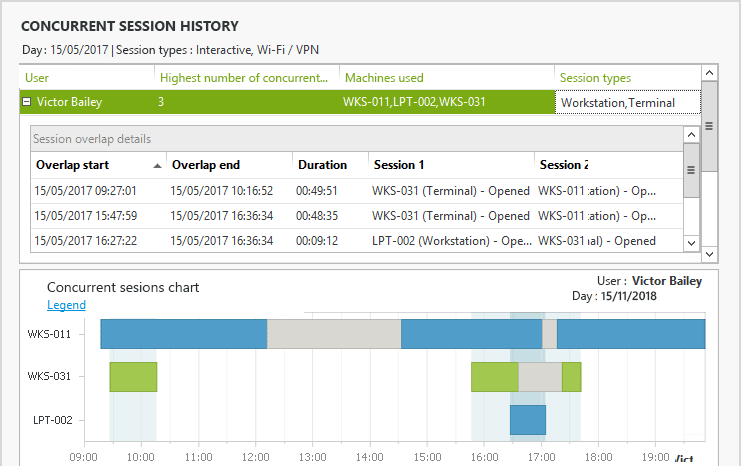
- Simultaneous connections: Limit concurrent logins and initial access points
Monitor, Alert & Respond to Login Behavior:- Get real-time visibility and insights into all user access. Interact and respond to any session, direct from the console.
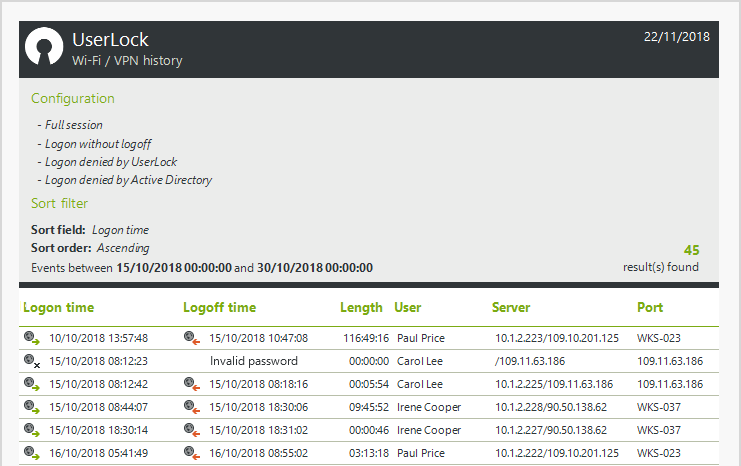
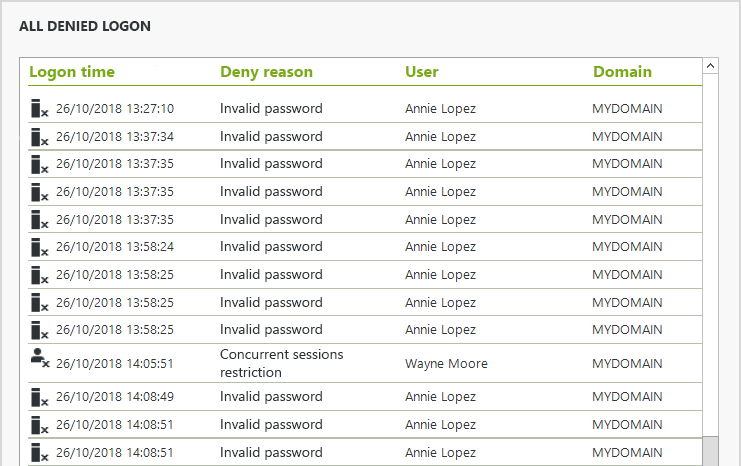
User Login Reporting:- A centralized audit for reports on all Active Directory user login events and attempts. Prove regulatory compliance, support forensics, and track down threats.
How it works
UserLock continuously monitors all network logon events, across all session types (including Wi-Fi, VPN and IIS), automatically applying custom policies to permit or deny authenticated users’ access. It allows you to track, report and immediately respond to any suspicious logon behavior, whether it originates on a PC, laptop, tablet or smartphone.
Easy to install, easy to use
You can install UserLock in minutes on a standard Windows Server. Microsoft-certified for compliance and support with Windows workstations and Windows Server, it works with Active Directory to read information but does not modify anything regarding accounts or schema.
UserLock – Key Benefits
Protect Passwords and Credentials:- Active Directory accounts are effortlessly compromised. It only takes a careless employee to share a password or leave a workstation unattended. Even the most careful employee can be exploited and the victim of stolen credentials. Stop uncontrolled and unauthorized access with UserLock, before damage is done.
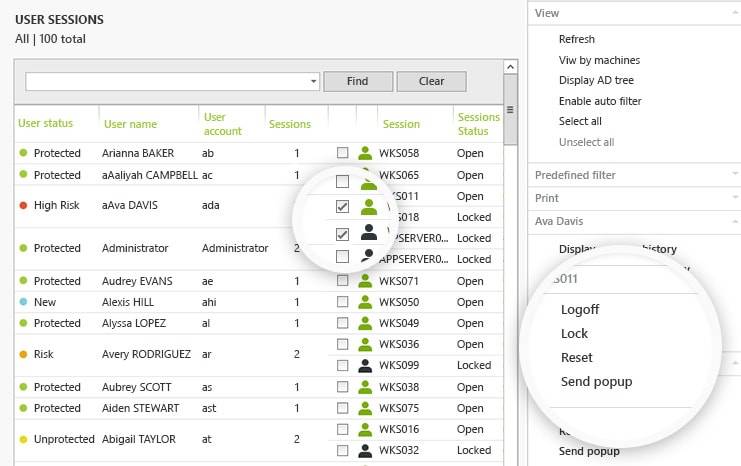
Manage Windows User Sessions:- With full visibility and insight into all Windows sessions, UserLock can interact remotely with any session (open or locked), direct from the console. Administrators can now logoff, lock or reset appropriate settings to manage shared machines, react to forgotten sessions left open, report on working hours, block suspicious behavior
Get Compliant on Securing Access:- Many standards are keenly aware of the importance of securing all logons. Requirements exist to ensure the access and usage of data are identifiable, audited, and attributed to an individual user. This software can both monitor this requirement, as well as stop inappropriate access from ever happening.
Avoid Network & Data Breaches: – By adding two-factor authentication, access policies, restrictions, and real-time insight around Active Directory user logins, this software helps ensure only the appropriate use of critical systems and sensitive data. And unlike security solutions that require an attacker (internal or external) to perform some kind of damaging action, it acts before any access is achieved and before damage is done* – no logon, no threat.
Prevent insider threats:- With UserLock, the ability to successfully logon (and remain logged on) becomes more than just whether the right credentials are used.
- Controls make genuine, but compromised employee logins, useless to attackers. Protect exploited users from phishing attacks or malicious colleagues.
- Out-rightly restrict certain careless user behavior such as password sharing, shared workstations left unlocked or logging into multiple computers.
- All access is identifiable and attributed to one single user. This accountability discourages malicious users, and offers a quick response and evidence to address violations that do occur.
Stop external attacks and lateral movement:- UserLock stops an attacker’s ability to use compromised credentials at the point of intrusion and as they move laterally within the network in an effort to find, access, and steal data.
Manage a controlled access policy:- Set different login limitations to ensure every user has sufficient access rights to fully perform their tasks, but no more. Being automated restrictions, this avoids the storm of alerts that turn out to be false positives. If something should fall outside of the established policies, UserLock automatically takes action – not only when IT intervenes.
Put a stop to password sharing:- UserLock mitigates the risk by making shared logins virtually impossible to use, except for the genuine owner of the password. Limiting simultaneous logins from different initial access points also deters those users who do continue to share, as it impacts their own ability to access the network.
Secure wireless & remote user access:- UserLock takes into consideration access from all session types and devices. It permits an organization to better control and restricts access to their wireless networks and user connections from outside the domain.
Protect any account with privileged access:- Every user has attributed access rights and privileges and is some sort of privileged user. UserLock ensures all accounts can’t be misused. It simultaneously enhances the access security of the most privileged users. For example, out-rightly restricting domain admin accounts to troubleshoot workstations.
Session monitoring and response:- Rather than investing in another tool, UserLock allows administrators to monitor and interact remotely with any user session direct from the console. Reduce the time spent on tracking user activity by up to 90%.
Accurate logon logoff forensics:- A centralized and searchable audit trail makes it easy to perform accurate forensics or prove regulatory compliance – freeing up time and resources for other critical tasks.
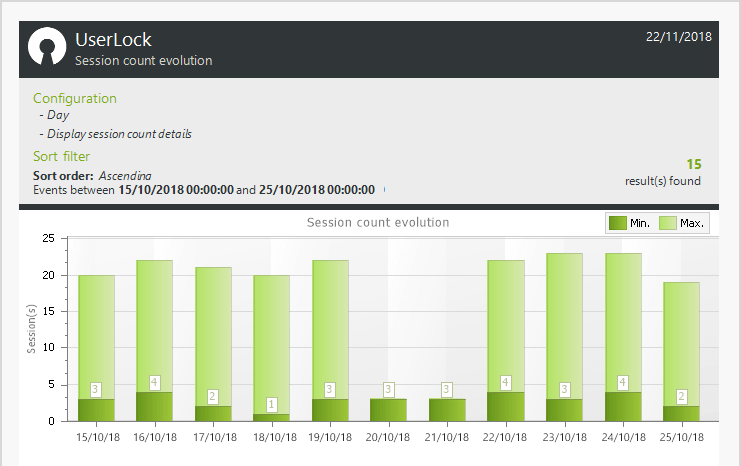
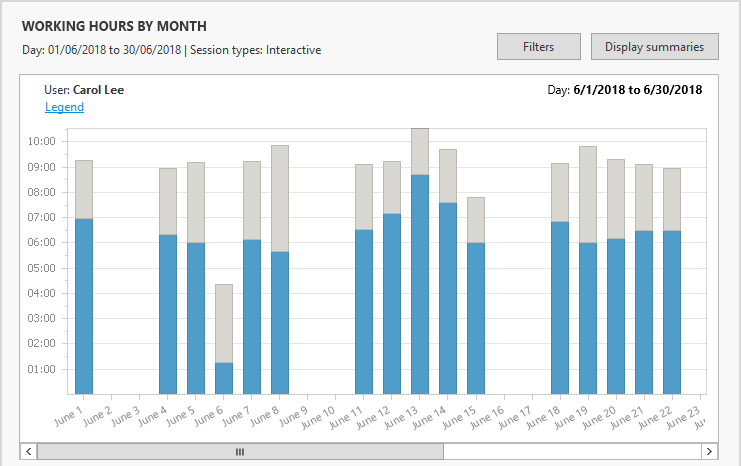
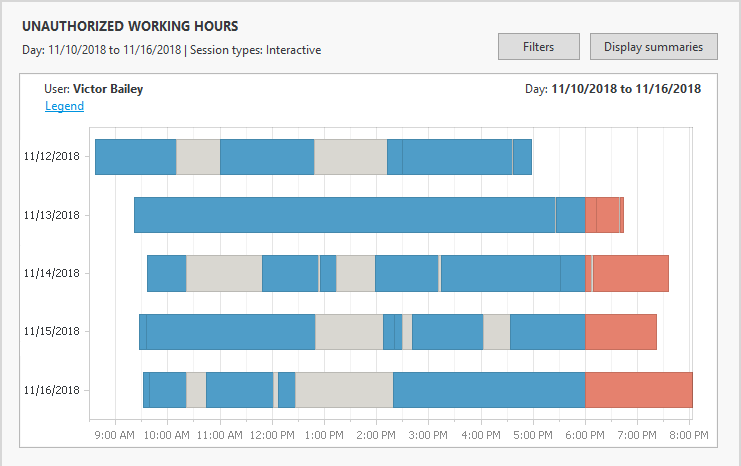
Manage working hours:- Accurate reports on the actual work hours allow you to better manage and react to employee’s attendance, overtime thresholds, suspicious access times, and more.
DataSheet & Solution Brief
You can download the UserLock solution brief here
You can download the datasheet here