- September 14, 2020
- Posted by: admin
- Category: 2FA for Windows
Two-factor authentication (2FA for Windows & RDP logins) with UserLock makes securing access to your Windows environment intuitive and easy. Get the best of both worlds – a secure network and a productive workforce.
12 Reasons to choose 2FA for Windows using UserLock
1) Deploy 2FA alongside Active Directory:- Simple to implement and intuitive to manage, UserLock 2FA for Windows works seamlessly alongside your existing investment in Microsoft on-premise Active Directory infrastructure. No modifications are made to accounts, structure, or schema.
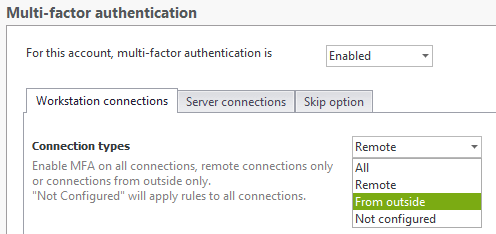
2) 2FA for Remote Desktop Connections:- Choose to enable 2FA on remote connections. End-users connecting to another machine (remote computer or virtual machine) within the network, can still receive a 2FA challenge. Administrators can choose to either apply 2FA for Windows on RDP logons that originate from outside the corporate network, or for every RDP login both internal and external.
3) Consider RD Gateway IP address as outside the network:- Remote Desktop Gateway (RDG or RD Gateway) enables network access for remote users, over the internet. By utilizing the Remote Desktop and the HTTPS protocol it creates a secure encrypted connection.
RDP connections that pass through a gateway, are by default considered as coming from ‘inside’ the network. To consider them as outside connections, simply list the RD Gateway IP address in UserLock’s advanced settings. You can then choose to enable MFA only for RDP logons that originate outside the network – and be sure to include all RD Gateway connections.
4) 2FA with Time-based or HMAC-based One-Time Passwords (TOTP and HOTP):- UserLock 2FA for Windows leverages authenticator applications or programmable hardware tokens to generate a One-Time Password for strong two-factor authentication. In both TOTP and HOTP, the token (the OTP generator) generates a numeric code. The security of OTP is based on fact that the codes are constantly changing and that they are single-use, hence the name. HOTP works just like TOTP, except that an authentication counter is used instead of timestamp.
Different options exist. Using a smartphone as a secure token frees the users from carrying a dedicated token device. This is often thought of as the best balance of security, usability, and cost available today. Programmable hardware tokens can act as a “drop-in” replacement of mobile apps. They are a great way to implement MFA for end-users who cannot use a corporate phone.
A hardware token can also be an external device you plug into your USB port and will automatically type in the OTP key for you. The user just has to tap their device, making the user experience even more frictionless.
5) Customize how you ask for 2FA:- For any user, user group, or OU, you can specify the circumstances under which 2FA is asked: by connection type, workstation or server connections and the frequency (every connection, every N days, first login of the day, every new machine).
6) 2FA for all users, including the most privileged accounts:- Securing access from all users aligns with most company’s desire to protect any Active Directory account with access to critical data and applications. It also improves your ability to restrict and respond to the most privileged of accounts – Windows local administrator accounts, domain admin accounts, Active Directory service accounts.
7) Secure, always available, on-premise hosting:- UserLock 2FA for Windows is installed on your own on-premise environment for maximum security and can be administered from any workstation remotely. Get insights, alerts, and reports on all 2FA activity across your organization.
8) One-click response to help end-users:- From the console, administrators can easily interact with any session and respond, reset or bypass authentication settings for any specific user.
9) 2FA in conjunction with contextual restrictions:- With UserLock’s contextual restrictions in place, administrators can be confident in customizing 2FA for Windows controls that avoid prompting the user for a second authentication, each time they log in.
Transparent to the end-user, they create a significant barrier to any attacker but don’t impede on employee productivity. They also help administrators distinguish legitimate asks to bypass or reset 2FA for Windows. Contextual factors include location, machine, time, session type, and the number of concurrent sessions.
10) Easy for both users and administrators:- Enrollment is intuitive and simple for users to do on their own. Alerts to warn end-users themselves when their own credentials are used (successfully or not) helps empower users to take responsibility for their own trusted access. Help requests alert administrators in real-time, who can immediately respond with one-click actions, allowing users to get on with their job.
11) Offline 2FA:- UserLock 2FA for Windows offers a complete on-premise solution, where no internet access is needed. User authentication for your employees is possible just about everywhere.
12) Cost-effective 2FA:- 2FA doesn’t have to come at a high cost – but it does have to be effective in relation to its cost. UserLock offers enterprise-caliber 2FA for Windows in terms of focus and effectiveness, but with SMB sensibilities in terms of implementation and use.
UserLock offers five primary functions, all working together, to secure access to a Windows Active Directory environment.
Two-factor Authentication (2FA) – Secure two-factor authentication on Windows logon, RDP, and VPN connections. Define the circumstances to verify the identity of all users, using one-time passwords.
Contextual Access Policy & Restrictions – Restrictions can be established to limit when an account can logon, from which machines, devices, or IP addresses, using only approved session types (including Wi-Fi, VPN, and IIS) and the number of concurrent sessions, etc. helping to reduce the risk of inappropriate use.
Real-Time Monitoring & Reporting – Every logon is monitored and tested against existing policies to determine if a logon should be allowed. Full visibility gives insight into any anomalous account behavior that may indicate a potential threat. Reporting helps ensure detailed insights for any investigations.
IT and End-User Alerting – Notifies IT and the user themselves of inappropriate logon activity and failed attempts.
Immediate Response – Allows IT to interact with a suspect session, to lock the console, log off the user, or even block them from further logons.